Agile security operations: three easy ideas to get started
A look at three simple ideas to ease your team into agile security operations

Agile security operations is about implementing an adaptive and iterative approach to monitoring information systems and networks. The goal is to make security operations more adaptable, collaborative and responsive to emerging threats and vulnerabilities.
In the context of security operations, agile can speed up the delivery of impactful monitoring services while maximising value-adding for business stakeholders. Moreover, it can improve alignment with engineering teams so monitoring technologies can continuously evolve.
Security operations centres (SOCs) often operate in the background and within a highly technical context. Moreover, they must deliver operational services under the pressures of service-level objectives. With limited time and visibility, they are always at risk of siloing themselves from the rest of the business.
Implementing agile across a cybersecurity program is a challenging journey. The same challenges become more acute when applying agile specifically to security operations. Delivery pressures and lack of time make responders and analysts less inclined to invest in transformative efforts.
Because of this, agile practices must be introduced gradually and wisely within security operations. Fortunately, there is no need for complex transformations to introduce agile within security operations. Often, change can start with a few small steps that eventually snowball into a larger shift.
If you aim to introduce agile to your security operations, there are three easy ideas to get you started. They are cheap to implement and typically less likely to encounter resistance. These ideas are called kanban, handshake protocol and retrospective.
Embrace rapid SOC servicing with Kanban
Kanban and agile are related but not the same. Agile is a project management philosophy that emphasizes flexibility, collaboration, and iterative progress, while kanban is a specific methodology often used within agile practices.
Invented by Toyota, kanban is the perfect methodology to improve the servicing of your SOCs needs without imposing excessive transformational burdens. Kanban, in fact, doesn’t require the introduction of agile principles within your team’s workflow.
Kanban simply requires the introduction of a kanban board. Here, analysts and responders can quickly capture ideas that will help them save calories on the job, such as incident response automations, alert enrichment routines or detection improvements.
The board is organized into columns (such as “To Do,” “In Progress,” and “Done”) that represent stages in the workflow. Each task or issue appears as a “card” that can be moved across columns as it progresses.
By using this column view, a kanban board allows teams to set limits on the number of tasks allowed in each column to avoid overloading team members. This helps maintain a smooth workflow by highlighting bottlenecks before they start impacting delivery speeds.
From the kanban board, your SOC engineering team can directly pick up prioritised requests and continuously deliver them without following rigid agile iterations. Using kanban, the SOC can continuously send feedback to engineering while receiving a constant servicing flow in return.
A rapid servicing methodology is crucial for your engineering and SOC teams to embrace iterative progress, continuous feedback and rapid response to emerging threats or vulnerabilities. This way of working provides the perfect way to ease your teams into agile with minimal disruption.
Today, launching a kanban board for your SOC should not be complicated. There are plenty of tools available on the market today, such as:
- Kanban JIRA: Jira is a project management platform developed by Atlassian which offers a Kanban-based solution. If you work for an enterprise, chances are that a corporate JIRA subscription is available for your team to use. The advantage of using kanban within JIRA is that you can leverage Atlassian’s wider suite of project management tools, such as the Confluence wiki platform, to scale your team’s project management capabilities over time
- Teamhood: If you are a smaller team, you may be better serviced by a slightly cheaper solution that doesn’t compromise on features or capabilities. Teamhood.com is a kanban-first, lean project management tool for service providers. For small teams, it is usually more cost-efficient than JIRA. However, as your team grows, Teamhood costs will quickly align with JIRA’s
- Nullboard: If you are concerned about sharing sensitive engineering requirements from your security operations with a third-party provider, you could opt for a self-hosted kanban solution. Nullboard is a free, open-source alternative, that also offers a dockerised version that can be self-hosted. While Nullboard is not an enterprise-grade tool, it can help in cases where your team is just experimenting or getting started in their kanban journey.
Enable close collaboration with handshakes
While a kanban board enables your SOC to report engineering requirements, weekly handshake protocols allow your SOC and engineering team to build alignment over priorities and progress.
A handshake protocol has nothing to do with agile. However, it is a powerful instrument to help alignment between your engineering team with the SOC. Interestingly, it will help teams embrace agile principles such as service transparency, consistent collaboration, inspection of deliverables and rapid adaptation to changing requirements.
Handshake protocols should occur once a week. These meetings should not last more than one hour, start on time and follow meeting best practices. They should energise both teams and help keep SOC services running smoothly. More importantly, they should contain a well-defined structure that covers, at a minimum, the below discussion sections:
| Section title | Description | Duration |
|---|---|---|
| Kick-off + sitrep | Sharing name of on-duty engineer. Sharing name of on-call analyst. Reviewing development KPIs |
5 mins |
| Topics discussion | Discussing all operational topics and new requirements to be added to the backlog. Note: Topics are provided before the handshake takes place. No more than 2 minutes are dedicated per topic. A maximum of 6 topics are discussed, including sharing feedback |
30 mins |
| Backlog refinement | The backlog for the weeks is reviewed and issue priorities are reassessed. The aim of the section is to agree the backlog of work to be performed during the week |
15 mins |
| Detections review | Detections that are to be released to production are reviewed and approved by the security operations team. Feedback on exising detections is exchanged and any fine-tuning requirements are added to the backlog |
10 mins |
All outcomes of discussions in the weekly protocol should be noted by the facilitator and uploaded to an internal wiki page immediately after the meeting. By meeting once a week and following a structured approach, your SOC and engineering team will maintain a constantly refined backlog.
Moreover, handshake protocols ensure that critical and high-urgency requirements are discussed and prioritised weekly. This is critical to ensure the engineering team can rapidly address urgent SOC requirements. By adopting handshake protocols, your SOC can raise quality issues affecting tooling or detections impacting operations, and have them properly fixed within days.
Finally, by starting the meeting with a discussion on development KPIs, both teams can review the engineering workload and cooperate to keep development pressures under control.
Encourage continuous improvement
A kanban board and regular handshake protocol will introduce a just-in-time engineering culture that keeps the SOC constantly fed and watered. Combined, they promote operational improvements. However, they won’t give the opportunity to evaluate overall performance from a service-level perspective.
That’s where retrospectives come in. These are structured review sessions where a team reflects on past work, identifying what went well, what could be improved, and how to enhance future performance. For security operations teams, retrospectives are particularly valuable as they provide dedicated time to analyze daily operations, discuss response effectiveness, and improve workflows to strengthen overall security posture.
Through open discussion, teams can surface recurring issues, share lessons learned, and implement preventive measures that reduce future risks. Additionally, retrospectives can help surface macroscopic operational challenges, such as lack of resources, lack of visibility within the corporate network or absence of critical tooling.
Retrospectives are simple to organise: set a clear agenda that outlines the goals, expectations and rules of the session. Schedule retrospectives at a time when all team members can attend. Finally, ensure the session is facilitated by an experienced, respected and trusted SOC lead.
To be effective, retrospectives must produce focused discussions. To do this, retrospective sessions must always start with a brief review of objectives and goals. They must also be structured around three discussion phases. To guide feedback, these phases should cover three topics covering “What went well,” “What didn’t go well,” and “What can be improved”.
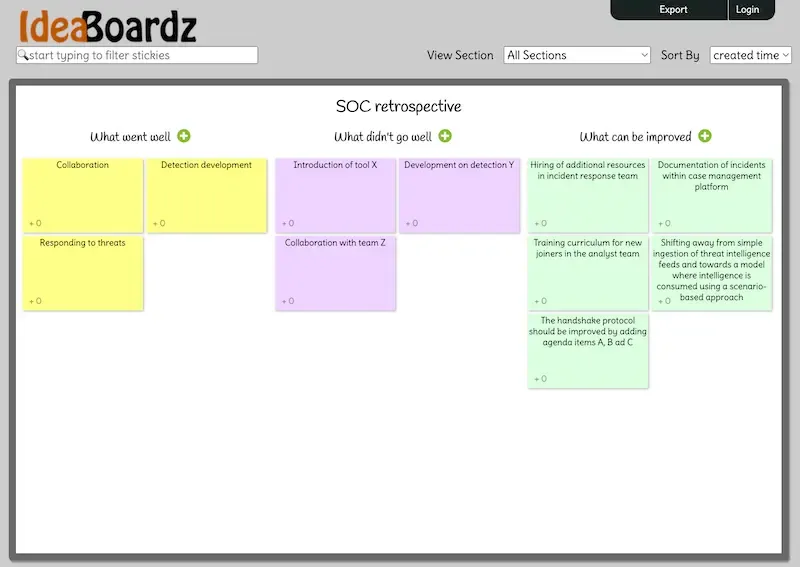
The facilitator must moderate the session according to a few simple rules. Communications must be candid, but open and respectful, ensuring everyone has the chance to speak. When speaking, team members must be encouraged not only to share improvements but also to constructively dissent by asking probing questions.
Once feedback has been captured, individual feedback points can also be clustered into feedback themes. Additionally, team members can vote on feedback items to help facilitators and managers identify improvements of high priority or importance.
Finally, the facilitator must summarise all key discussion points and record actionable items. At the end of the session, responsibilities and follow-up dates must be agreed upon to ensure improvements are implemented. When concluding, the facilitator must express appreciation for everyone’s insights, reinforcing a culture of continuous improvement.
The strength of retrospectives is that they can be run alone by your SOC or jointly with engineering teams or stakeholders. In the first case, a retrospective can help the SOC reflect on internal challenges. In the second case, a retrospective can help surface challenges in SOC servicing, collaboration or stakeholder satisfaction.
Conclusion
You don’t need to embark on a time-intensive and politically expensive transformation to adopt agile security operations. You can initiate a gradual shift by adopting a few easy-to-implement methods to get your teams operating in line with agile principles.
Kanban will provide your SOC team with a visual, task-driven approach to streamline operations and address high-priority issues without requiring intensive efforts such as operating model changes or aligning job functions with agile roles.
Handshake protocols will create regular, structured meetings for SOC and engineering teams to align on tasks, ensuring a smooth workflow and promoting a just-in-time engineering culture.
Finally, retrospectives will offer your SOC dedicated time to review and refine overall performance, capturing lessons from daily operations and identifying areas for improvement.
Together, these three simple changes will foster responsiveness, continuous improvement, and enhanced collaboration between SOCs and engineering, ultimately improving overall agility and service delivery with minimal disruption.