How to build a free ISMS with ChatGPT
ChatGPT can accelerate the creation of a free Information Security Management System. Find out how in this post
ChatGPT is generating a large impact on many sectors and industries. From education and business to entertainment and publishing, this technology is accelerating many repetitive tasks that once required many hours of human work.
ChatGPT is also proving useful in the cybersecurity industry. Many vendors are in fact integrating ChatGPT capabilities within their tools in order to provide enhanced threat detection, automating security tasks and improving vulnerability management.
However, most of these advanced applications are still either under development or accessible to smaller groups of paying customers. However, there are other areas where ChatGPT can immediately help smaller cybersecurity teams. For example, ChatGPT can greatly accelerate the production of documentation and policies.
The underlying technology behind ChatGPT is a transformer-based neural network architecture. Transformer neural networks are a type of neural network that is specifically designed for processing natural language data. They are able to learn long-range dependencies in text, which allows them to understand the context of a sentence or paragraph more effectively.
ChatGPT has been trained on a massive dataset of text and code. This dataset includes books, articles, code, and other types of text, with large amounts of data also covering cybersecurity materials. The training process involved feeding the dataset to the transformer neural network and allowing it to learn the patterns and relationships in the data.
Once the transformer neural network is trained, it can be used to generate text, translate languages, write different kinds of creative content, and answer questions in an informative way.
As a result, ChatGPT can be used to automatically create documentation. More importantly, with some expert prompting, ChatGPT can be instructed to build more sophisticated forms of documentation such as an Information Security Management System, or ISMS in short.
Why build an ISMS with ChatGPT
An ISMS forms the backbone of a company’s information security. I’s a framework for managing information security risks and it helps companies enforce a systematic approach to managing the confidentiality, integrity, and availability of information assets.
An ISMS can be implemented by organizations of all sizes and in all industries. It is a valuable tool for protecting information assets from cyber threats and other security risks.
There are a number of benefits to implementing an ISMS. The primary one for companies is reducing the risk of cyber attacks and data breaches as well as improving compliance with regulations and promoting an increase in customer and investor confidence.
The most common standard for building an ISMS is ISO/IEC 27001, with the most recent version being released in 2022. This standard provides a comprehensive framework for managing information security risks and is recognized by organizations around the world. Moreover it is used by many businesses as the foundation to achieve ISO 27001 certification.
There are many resources available to help companies looking to implement an ISMS. There are also many consultants and service providers who can help with the implementation process. Unfortunately, implementing an ISMS can be an expensive endeavour, especially for large organisations with complex IT systems.
Costs can also quickly accumulate for small and medium enterprises: the ISO 27001 standard itself is quite comprehensive and it can take maky months for a small team to write an ISMS. The implementation of an ISMS will take even longer regardless of how efficient a security team is in writing the ISMS.
Fortunately, by cutting the time it takes to design and write an ISMS, security teams can limit ISMS costs largely to the implementation/operationalisation phase. ChatGPT can play a huge part in the first ISMS writing phase.
How to build a free ISMS with ChatGPT
Want to cut to the chase? Then subscribe to the blog to download the Ultimate ChatGPT ISMS prompting cheatsheet to get building fast!
In order to build an ISMS it is important to know how to submit queries to ChatGPT. Effective querying will result in better and more precise outputs. With effective querying the goal is to minimise the amount of time it takes to fine-tune the policies that ChatGPT produces. By getting the tool to output policies that have the proper structure and content, we can avoid wasting time having to rewrite policies over and over again.
When building an ISMS with ChatGPT there are several types of prompts that are useful to know. Specifically, these are:
- Directive prompts: these prompts provide ChatGPT with clear, specific instructions and guidelines when building your ISMS policies. Examples of directive prompts include queries such as “Detail the steps for reporting security incidents”
- Informational prompts: these prompts instruct ChatGPT to package together information on various aspects of the ISO27001 standard and its underlying ISMS policies. They are useful from a research and guidance perspective. An example informational prompt could be “Provide an overview of the key components of an ISMS, and how they work together to ensure information security”
- Descriptive prompts: these primpts are useful when ChatGPT outputs policies and procedures that are lacking detail. You can recursively use these prompts to ask ChatGpt to fine-tune the details of specific policies and their provisions, for example: “Explain the process of conducting a data classification assessment. What criteria are typically used to classify data in an organization?”
When building an ISMS with ChatGPT it is also important to know what to query for. Here, two considerations are important: first, we need to understand the basic structure of an ISMS in order to submit the right prompts. Secondly, we need to know how the internals of the ISMS policies themselves must be structured. By knowing these details we can ensure policies contain the exact content needed.
Basic structure of an ISMS
An ISMS needs to be structured around the standards outlined in ISO/IEC 27001. The standard defines a series of mandatory sections needed for the underlying framework to properly guide the operation of the ISMS. These sections will help the ISMS align with business goals, stakeholder expectations and promote security best practices in the organisation.
For an ISMS to be effective it must be built in a manner that follows the Plan, Do, Check and Act (PDCA) cycle. This cycle provides organisations with a simple and effective approach to problem solving and managing changes. By structuring the ISMS around the PDCA cycle we build a framework that embeds a continuous loop of planning, doing, testing and continuous improvement within its foundations.
Based on these requirements we can define our core ISMS structure as follows:
Plan
This is the initial phase of the cycle and involves setting the foundation for the ISMS. During this phase, organizations establish the objectives, policies, and processes required to manage information security effectively. In the plan phase the below sections must be built:
- Section 4 context of the organisation: serves as the foundation for developing security policies, defining the scope of the ISMS, conducting risk assessments, and making informed decisions to protect sensitive information effectively
- Section 5 leadership: describes how company management is actively engaged in information security governance and supporting the lifecycle of the ISMS
- Section 6 planning: provides the strategic framework for information security. It guides the organization in defining its security objectives, assessing risks, allocating resources, and ensuring compliance
Do
In this phase, organizations put their planned strategies and processes into action by creating policies for the below sections:
- Section 7 support: provides the organizational structure, resources, and processes needed to establish, maintain, and continually improve information security.
- Section 8 operation: ensures that security controls are effectively enforced, incidents are managed, and information assets are protected on an ongoing basis, ultimately safeguarding an organization’s sensitive information
Check
In this phase organisations focus on monitoring and reviewing the ISMS to ensure it is operating as intended. To achieve this goal, organisations must create policies to cover ISO 27001 Section 9, which is called Performance evaluation.
Act
The final phase is about taking actions to improve the ISMS based on the results of the “Check” phase. This is achieved by defining the underlying policies of ISO 27001 Section 10. Unsuprisingly, this section is named the Improvement section.
Using the above structure as a guiding template, we can group our ChatGPT prompts accordingly and build the ISMS in conformity with the ISO 27001 standard and the PDCA cycle.
Finally, in order to operationalise the ISMS we will need to build policy documents that implement some of the essential information security controls listed within Annex A of ISO 27001. Specifically, policies for the below controls should be defined:
- Organisational controls: in this section we should create documents that define the organisation’s threat intelligence, asset management, information classification, access controls, supplier management and incident management policies
- Technological controls: in this section we should create the documentation to define the organisation’s vulnerability management, data protection, backup management, logging management, network management, cryptographic controls, penetration testing and change management policies
- People controls: in this section we should build an incident reporting and response policy
- Physical controls: in this section we should build a physical security policy for the organisation
Basic structure of an ISMS policy
When building our ISMS we also need to ensure that the policies follow a consistent strusture. By having a standard structure defined beforehand we can write queries to better direct ChatGPT when creating policy content. This will be especially important during the fine-tuning phase once the first version of each policy has been created.
While ChatGPT can build basic policy templates, it will often create policies that follow differing content structures. A defined structure can help correct ChatGPT when it starts producing overly creative policies, structurally speaking.
A good document structure to use when creating an ISMS policy could be as follows:
- Title and Table of contents: these two sections are self explanatory and would be used to help readers identify the document and navigate its content
- Document information: this is an important section of an ISMS policy document. It must be situated within the document first page and must contain, at a minimum, the name of the document owner, the document confidentiality classification (public, internal use or confidential), the document approval state (draft, in review, approved) and, finally, the document’s approval and last review dates
- Purpose, Area of application and User: this section of an ISMS policy sets the stage for the rest of the policy document by explaining its objectives, specifying where it applies, and identifying the intended audience. This information helps readers understand the policy’s context and their roles and responsibilities in maintaining the policy within the organization
- Reference documents: this section ensures that the reader of the policy is well-informed and can retrieve all external sources of information and policies referenced in the document
- Policy main body: this section would contain the main body of the policy
- Versioning table: this section would contain a table to list all major policy revisions and version releases
Crafting ChatGPT queries to create our ISMS
Armed with the above knowledge we can start submitting ChatGPT queries to create our ISMS. We can first start by asking ChatGPT to build the basic structure of our ISMS. As discussed, the core of the ISMS will contain documents conforming to all sections from 4 to 10 of the ISO 27001 standard.
Following the above best practices, we should strive to create queries that are short, sharp and to the point. For example:
Create an ISO 27001 leadership and committment policy
After reading such prompt, ChatGPT will proceed to create a draft of the requested policy. You can also direct ChatGPT to create policies in a format that is easily consumable by your systems. For example, you can ask ChatGPT to output content in markdown format to make it easily exportable to multiple word processing systems. This is easily achieved simply by specifying the output format within your prompts as shown in the below example:
In Markdown format, create an ISO 27001 leadership and committment policy
You can also use the same technique to build policies for your technological, organisational, people and physical controls. Using the same formula, ChatGPT will happily build your company’s control policies to supplement your ISMS. For example:
In Markdown format, create an ISO 27001 information classification policy
Using simple queries will help you rapidly build all the necessary ISMS policies in less than a working day. However, in some cases ChatGPT will produce overly skeletal policies that include the expected structure but require you to complete and fill out almost all sections and paragraphs of the policy. In some instances, ChatGPT may produce the wrong structure altogether. When this occurs you can provide further instructions to fine-tune the policy structure produced by ChatGPT. For example:
In Markdown format, create an ISO 27001 information security policy
that includes the purpose of the organisation, includes information security
objectives, includes a committment to satisfy applicable requirements
and contains a committment to continuous improvement in addition
to all other sections that are expected to be included in an
information security policy
The above prompt is obviously more verbose and complex, but it will give ChatGPT the necessary direction to create a policy that better conforms to the ISO 27001 standard. Verbose queries should be used with caution: as the verbosity of prompts increases you need to take special care in ensuring that your prompts remain precise. If you give ChatGPT excessive room for interpretation then the tool will most likely begin inventing sections or write too much “filler” content.
Avoid runnig into all the above problems and save time by downloading the Ultimate ChatGPT prompting cheatsheet. It’s designed to save you hours of troubleshooting, reviewing and prompt tweaking. It is also absolutely free for subscribers!
Limitations of using ChatGPT to build an ISMS
In order to use ChatGPT to its full potential its important to understand its limitations. There are at least four core limitations that you should be aware of:
- ChatGPT is only useful in accelerating the writing of an ISMS. ChatGPT will not operationalise the ISMS for you; for that you will need ISMS/Risk Management specialists
- Similarly, ChatGPT will not help with building a Statement of Applicability, an ISMS landing page, underlying risk treatment frameworks or ISMS key performance indicators that are specific to your organisation. All of these documents are necessary to get ISO 27001 certified
- The output of ChatGPT will still need to be reviewed and adapted to your organisation. You’ll save enormous amounts of time on the writing part, but you will have to put the work in to make sure the ISMS policies reflect your organisation’s operating environment
- In most cases, ChatGPT will fall back on repetitive policy structures and repeated content. If that happens, you have to invest time in writing more fulsome prompts in order to better instruct ChatGPT in producing the exact content you expect
Dangers of using ChatGPT to build an ISMS
ChatGPT should not be treated as a silver bullet when looking to build a first version of an ISMS. In its current form (and especially if the default, free GPT-3.5 version is used) ChatGPT can only accelerate the creation of an ISMS, not write it entirely from scratch without supervision or review.
In particular, anyone using ChatGPt to write ISMS policies must be aware of the below issues:
1. Invented content
ChatGPT requires the user to be familiar with ISO27001 normative annexes and the controls contained within. When asking very specific queries on the contents of the ISO27001 standard ChatGPT will often resort to inventing content. Expert eyes are needed to assess when the tool’s knowledge boundaries have been exhausted and it resorts to making stuff up.
As an example, consider section 5 of Annex A of ISO 27001. A simple review of the standard will reveal that section 5, called organisational controls, lists exactly 37 controls (from 5.1 to 5.37). However, if we ask ChatGPT to list such controls it will start listing a completely invented list, as seen in the screenshot below:
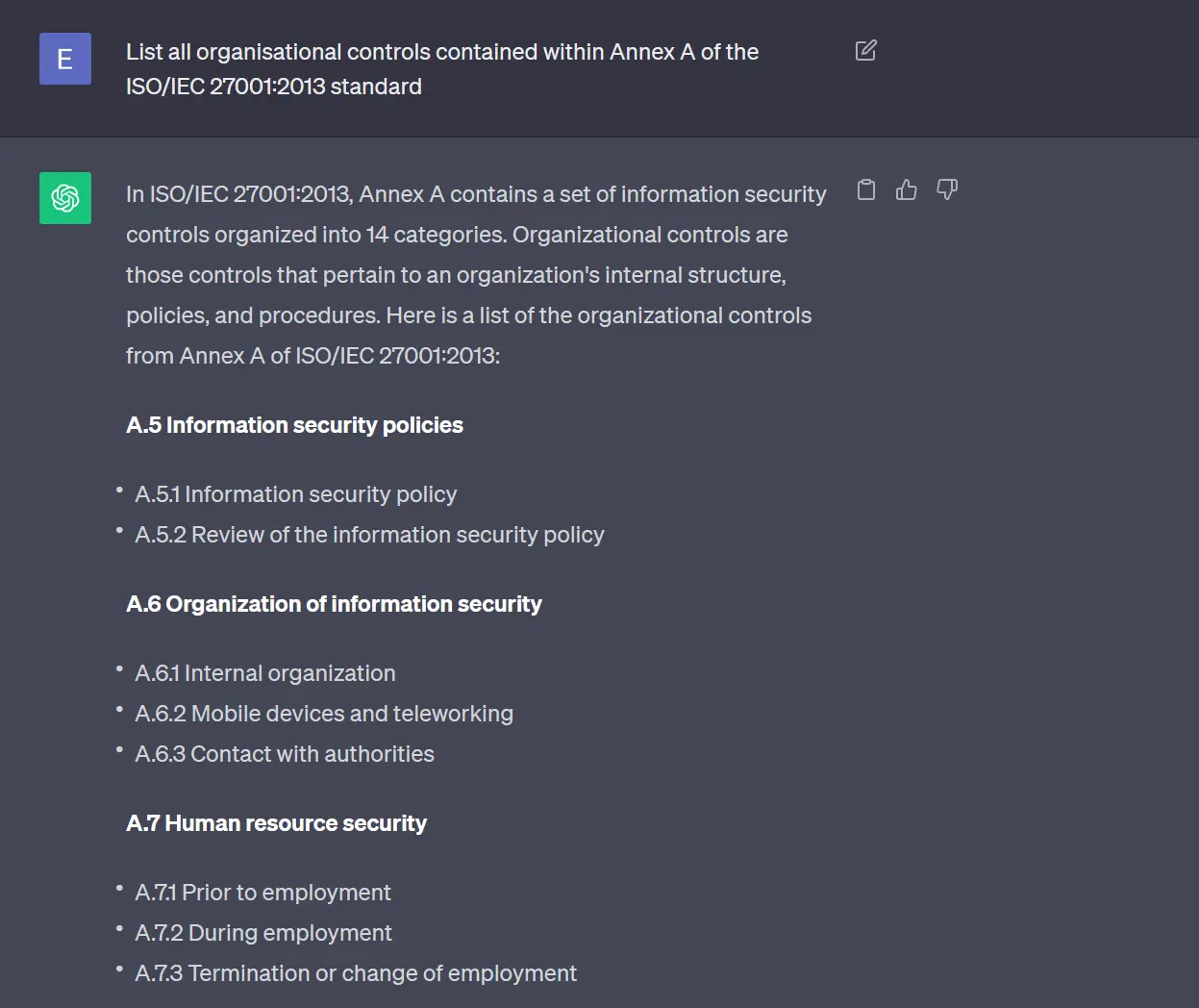
What’s worse is that ChatGPT will invent content by repackaging other legitimate sections of the ISO 27001 standard, thus making it harder for the untrained eye to spot what is going on.
2. Outdated content
It is easy to prove that ChatGPT has amassed its vast body of knowledge by crawling outdated content on the internet. In the context of ISO 27001 we can prove it by simply submitting the below prompt:
List all Annex A controls of the ISO27001:2022 standard
ChatGPT will respond with a (hilariously) incorrect answer that reveals it is only familiar with the outdated ISO 27001:2013 standard:
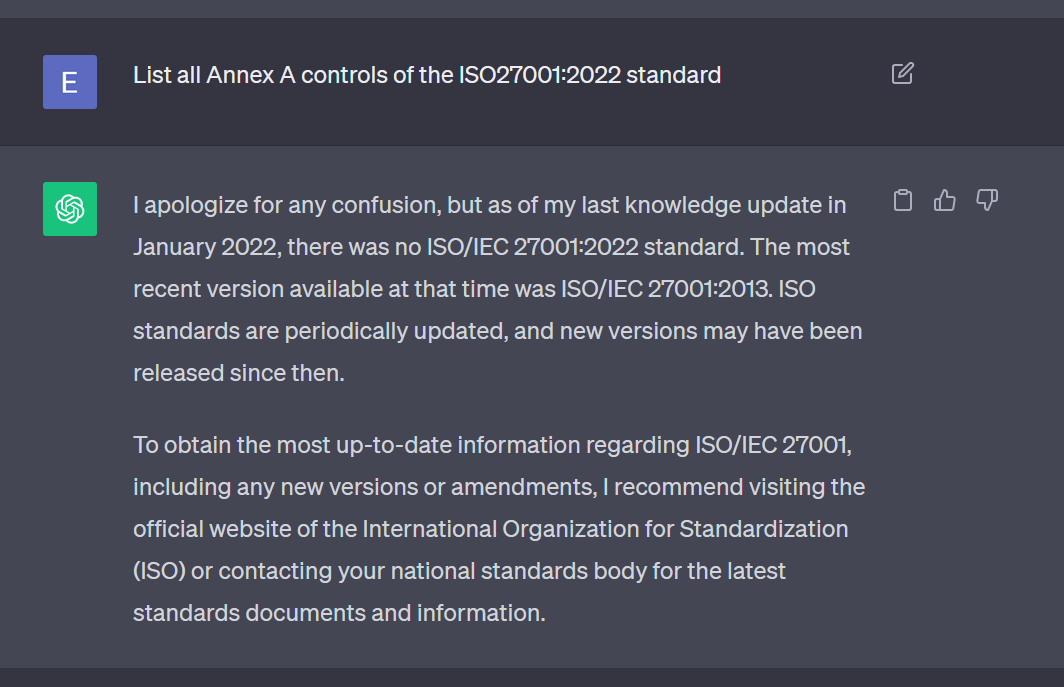
Any quick research on the internet will reveal that the ISO 27001:2013 standard has now been superseded by ISO27001:2022 and is two versions behind the latest version. On a side note, if you’d like to get a good overview of the changes introduced by the 2022 version, check out this excellent blog post by InfoGuard, a Swiss provider of Cybersecurity Services.
3. Confidentiality considerations
In the hands of a specialist, ChatGPT is an amazingly powerful tool that can significantly save time and costs. However, using it without control can introduce serious confidentiality risks.
In our specific case ChatGPT should be used strictly to build the basic structure of our ISMS and to draft the non-confidential part of our policies. However if, in an effort to correct ChatGPT output, you start creating prompts that outline internal company processes, you may inadvertently hand over sensitive information to ChatGPT.
When building your ISMS policies, be careful not to use prompts containing confdential information. Let ChatGPT build the outer structure and content of your policies and manually add all confidential policy details once you have extracted the draft policies from the ChatGPT user interface.
In conclusion, ChatGPT delivers best results if used by an individual with experience in creating ISMS systems for organisations. Such an individual can best prompt ChatGPT and correct any mistaken outputs. In its current state, ChatGPT simply cannot substitute the expertise of a certified ISO27001 consultant. It can only help your team when used specifically to accelerate the writing of your ISMS and nothing more.
