Cybersecurity budgeting basics
Learn how to build a budget that your CFO and management board can understand

The fourth quarter is budgeting time for most companies. Equally, most security managers are gearing up to support their CISO with preparing the security budget for the upcoming year.
Security budgeting is an overlooked area in the cybersecurity industry. It’s also an overlooked skill set when hiring and training cybersecurity executives. Yet, it is a crucial aspect of managing a cybersecurity program. Cybersecurity budgeting rests at the crossroads between cybersecurity (as a discipline) and business.
A well-executed budgeting round will drastically increase the standing of the CISO (and security team) in the eyes of management. The goal is to connect funding requests to objectives and initiatives that keep the business within agreed risk tolerances. When CISOs elegantly pull this off, they help create an understanding within the management board that every dollar and person in the security team represents a leveraged investment that ultimately protects or adds to the company’s bottom line.
Need a field-tested budgeting tool that your CFO can understand? By subscribing to Premium, you can download Blog on Security’s yearly budgeting tool whenever you want.
The fundamentals
The fundamentals of crafting a good cybersecurity budget can be neatly summarised in one picture:
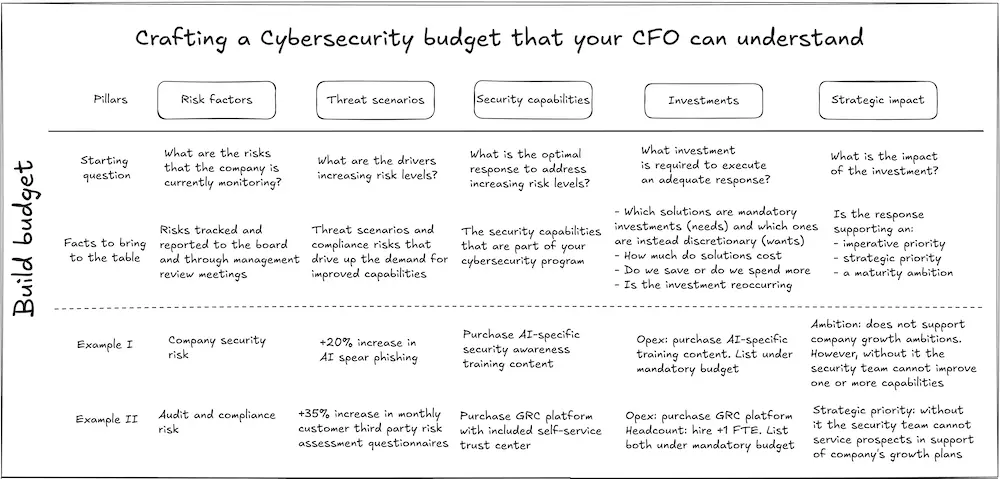
Looking at the above model, it is worth highlighting the foundational role that risk plays in building a solid cybersecurity budget. Management ultimately only cares about growth. Thus, risk becomes relevant only if it gets in the way of growth.
Building your budget from this fundamental starting point will help you:
- Capture management attention and increase your/your team’s credibility.
- Identify strategic initiatives that are getting the most funding.
- Tailor your security program to support well-funded initiatives and “take a share” from these initiatives (usually with more ease).
- Identify low-priority/low-funding areas where stronger business cases will be needed.
When building your budget around risk, keep complexity low by referencing the risks tracked through management reviews. Highlighting new risks will introduce additional learning curves within budget conversations and inevitably complicate discussions. If you must introduce new risks, prioritise those that hurt high-funding strategic growth initiatives.
When discussing risk, showcase tangible threat scenarios that impact growth. These will help management understand why money must be invested into specific risk-reduction capabilities. And while you are at it, use solid commercial narratives when highlighting optimal risk-reduction responses. Management will respond well to commercial narratives such as:
- Investment X will help increase capability Y to enable growth initiative Z (by addressing risks A, B, C).
- Investment X will help increase capability Y so we may continue to service compliance/customer/prospect security requirements.
- Investment X will help increase capability Y so we may reduce costs on capability Z (while addressing risk A, B, C).
Finally, a key success factor is cultivating a good relationship with your Chief Financial Officer (CFO). An excellent relationship with the CFO will be fundamental to constructive budget negotiations. Make sure to invest the time into building the relationship to reap the dividends when the budgeting quarter arrives.
Building an effective budgeting tool
An effective cybersecurity budgeting tool is key to successful negotiations. To be useful to both yourself and your CFO, a cybersecurity budgeting tool must fulfil three characteristics:
- It must provide a high-level, visual overview of the budget.
- It should include a supply/demand overview where growth-hindering risks and scenarios are mapped to the relevant security capabilities/risk-reduction initiatives.
- It must include a detailed budget inventory, where individual opex and headcount costs are listed.
Visualising your budget
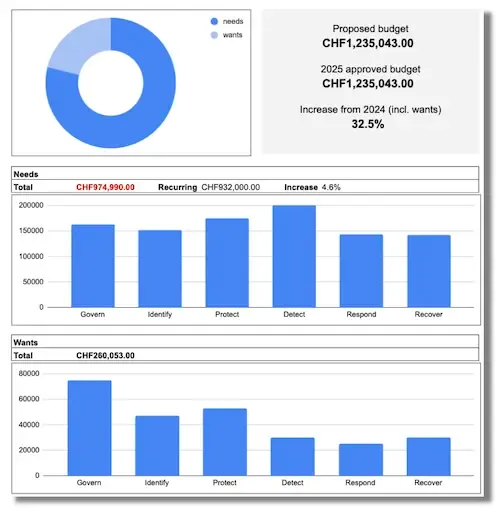
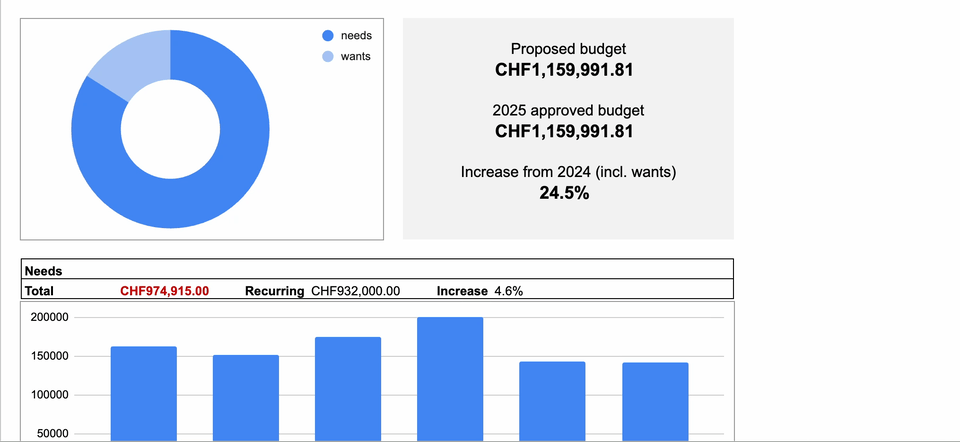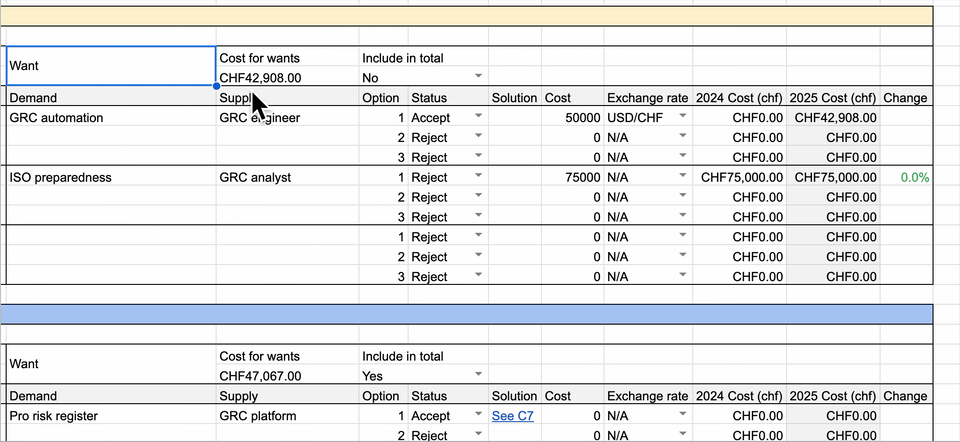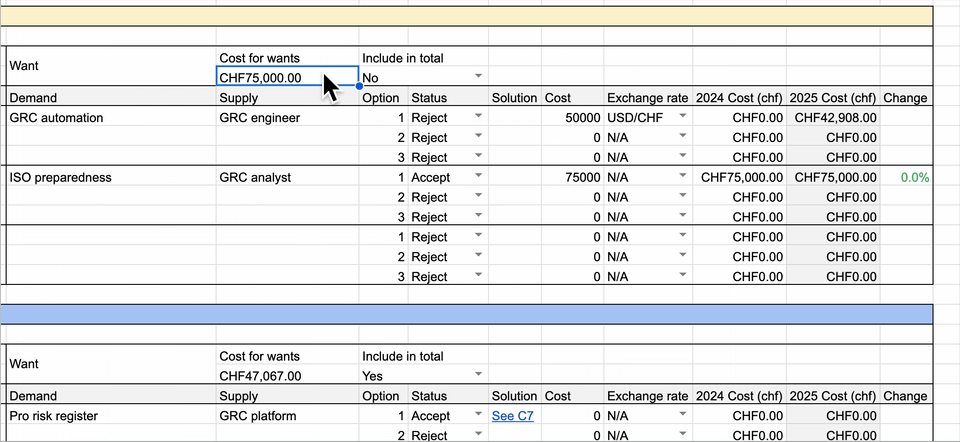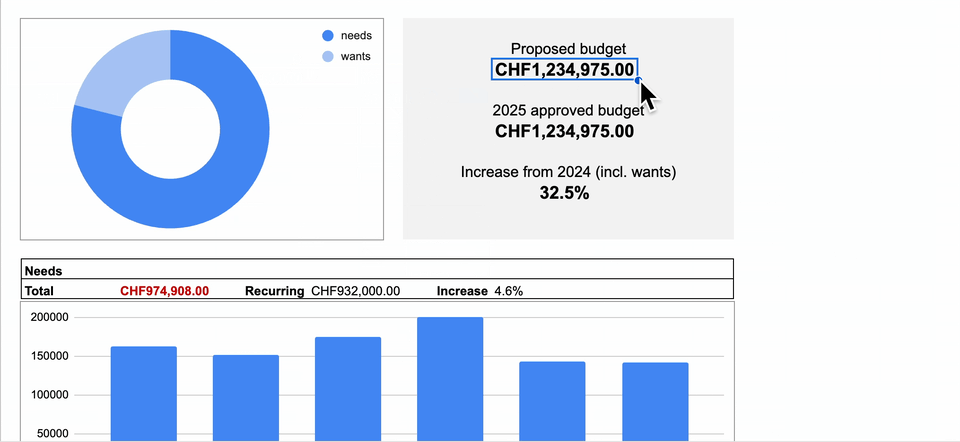
A visual overview needs to provide your CFO with the key facts to digest your budget request. The picture below showcases an example of an effective visual overview:
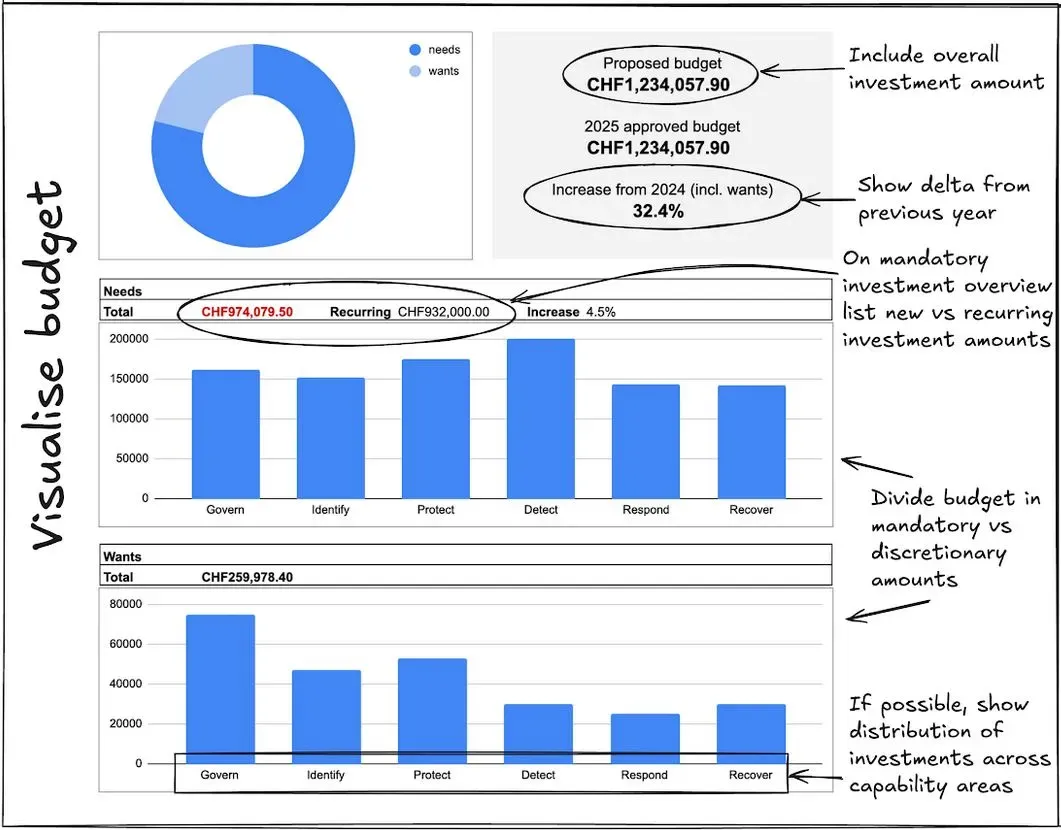
A couple of fundamental components are needed within the visual overview. Firstly, the overall investment amount must be shown. More importantly, you must include the delta (in percentage terms) compared to previous year’s spending. This is, in fact, one of the key figures that your CFO will be interested in.
Secondly, you should divide the budget into mandatory versus discretionary investments. This will help your CFO understand which part of the budget falls into the “must-have” category. Conversely, the discretionary section will show which investments fall into the “nice to have” category.
Thirdly, you should show the distribution of investment across security capabilities. Refrain from adding too much detail and keep the distribution overview as simple as possible. A good technique is to use the capability areas within the NIST cybersecurity framework as a starting point to summarise your internal security capabilities.
Finally, you must highlight recurring expenses and include these within your mandatory category. This will send the message to your CFO (and management team) that mandatory investments are to be viewed as part of the “cost of doing business safely and in a compliant manner”.
Documenting supply/demand
A solid understanding of the supply and demand dynamics driving your security budget is crucial. It will increase clarity of thought during the budgeting process while signalling to management that you are thinking commercially about how to manage (or reduce) any security budget expansions.
The goal is to document the demands coming from your team (or security programs/projects) and map them to a supply of resources and capabilities to meet those demands. By documenting supply and demand, you can then assess if both are broadly in balance.
If supply fully meets demand then you know you have developed a solid, well-justified budget. If there is an imbalance, this will be a signal that more thinking is required to balance any supply-side deficits.
Below is a simple, but effective, example of how supply and demand dynamics can be captured within a cybersecurity budgeting tool:
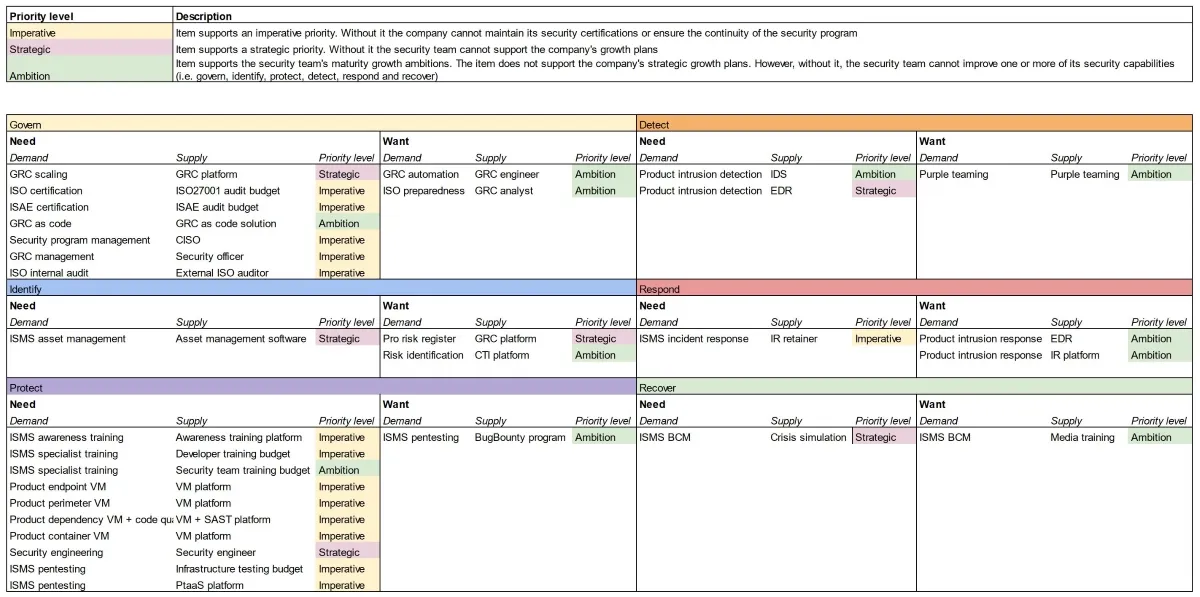
In this overview, you should list supply and demand items by security capability. Within each row, you should map a security team/program demand to the relevant supply of resources. If you want, you can include operating expenditures and headcount at the same time.
Additionally, you could also specify whether each item falls into a mandatory “must have” or a discretionary “nice to have”. Strictly speaking, this is not necessary. However, it will add an extra dimension to your overview highlighting optional supply and demand items that could be picked apart by your CFO.
More importantly, highlight the strategic impact of each budget item. Doing so allow you to justify and explain the level of impact of each investment on the company’s growth strategy. You can do so by categorising each budget item as belonging to one of the following categories:
- Imperative: these items support an imperative priority. Without them, the company cannot maintain its security certifications or ensure the continuity of the security program.
- Strategic: these support a strategic priority. While not imperative, without them, the security team cannot support the company’s growth plans.
- Ambition: these support the security team’s maturity growth ambitions. In principle, the item does not support the company’s strategic growth plans. However, without it, the security team cannot improve one or more of its security capabilities. Alternatively, without it, the security team will not be able to effectively reduce risk in business areas that have experienced a prolonged period of risk accumulation (for example, because in the preceding years some risks were persistently accepted).
By building your supply and demand overview this way, you will visualise all the dynamics driving your budgeting needs. More importantly, it will highlight those items of non-mandatory spending which have a strategic/ambitious flavour and that will require more attention during the negotiation rounds.
Creating a budget inventory
The inventory is the engine powering your entire yearly budget. It should build on top of the supply and demand overview to provide a detail account of all tooling and headcount spending options available for the year.
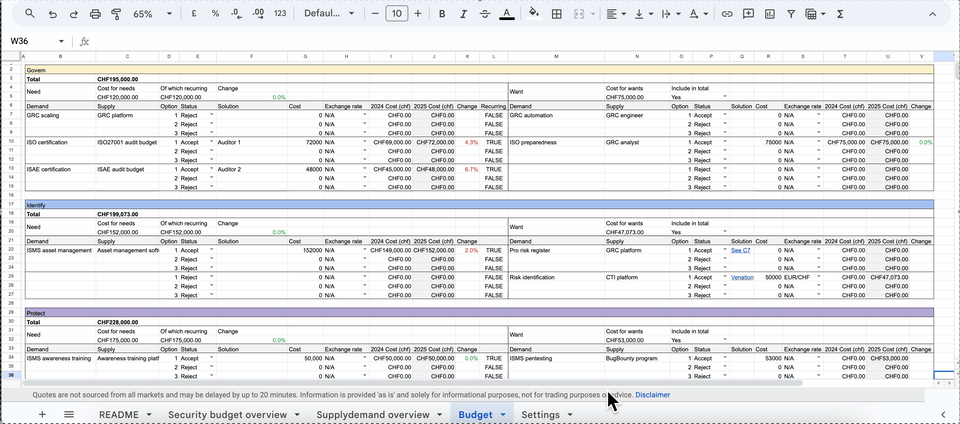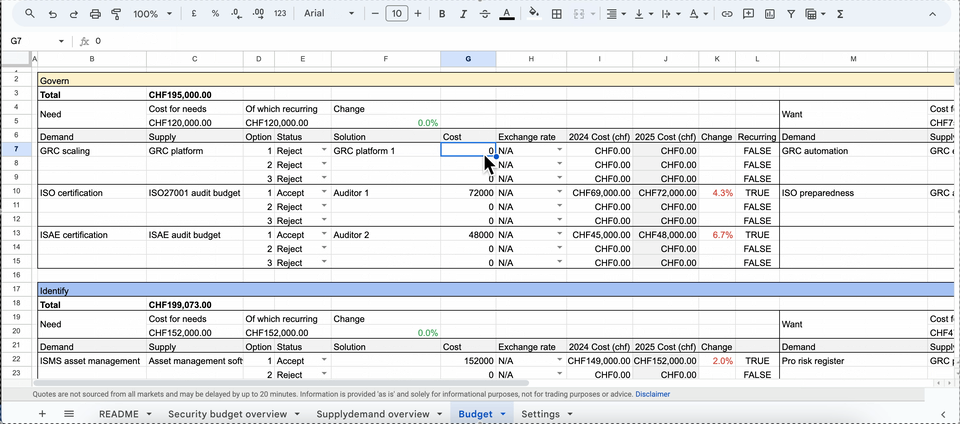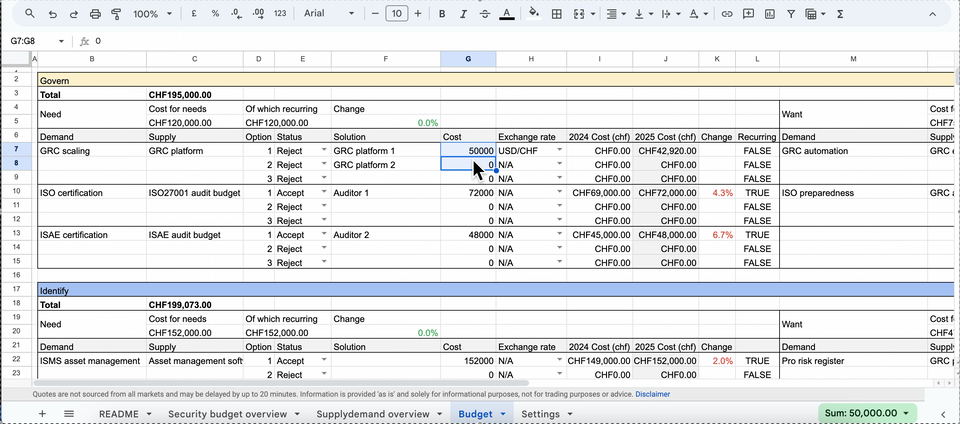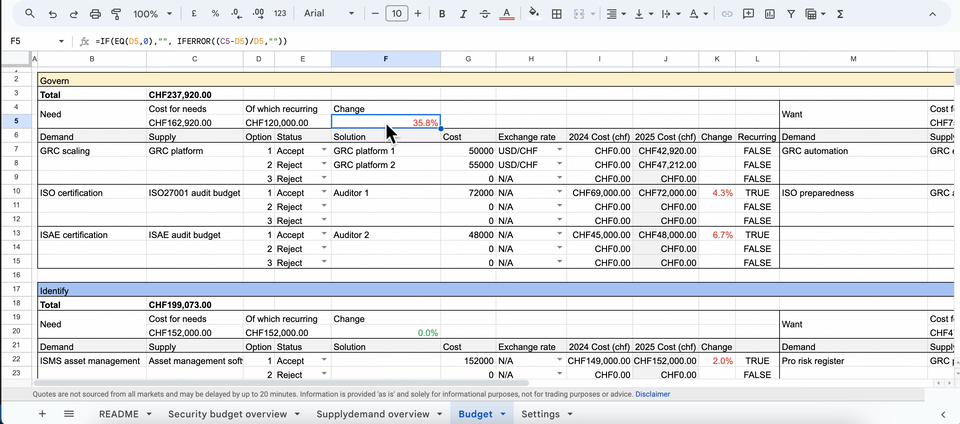
An effective inventory gives you and your team the ability to build the budget from the “ground up”. For each supply and demand factor, the budget should allow the listing of several funding options. Each option would capture a quote or project cost for a specific tool or headcount, enabling comparisons of different options and costs available from the market.
Once you identify an acceptable option (from a cost/benefits standpoint) you can include it within the overall budget request. Additionally, the inventory should allow you to convert costs to your local currency, highlight reoccurring spending items and view cost decreases or increases compared to the previous year.
Similarly, the inventory should list all funding options for your discretionary budget items. It should also include or exclude individual spending items from the overall discretionary budget amount. In addition, it should allow you to include and exclude overall discretionary budget funds by security capability, as seen below:
By using such an inventory, you’ll build a budget from the ground up that can be “sliced and diced” as needed to get the desired result. Additionally, it will allow you to focus into specific budget requests during negotiations with your CFO. With such a tool, you’ll have full command of your yearly budget requests, from high-level amounts down to individual spending options.
Pitching the budget
Once you have assembled your request in your budgeting tool, you must pitch your funding requirements to the board of directors. There are a couple of fundamental areas that you must include within your pitch:
- Overall introduction: when pitching your budget, always start by providing a refresher on the security risks being tracked by your security program. Map each tracked risk to your internal risk mitigation capabilities. Then, add a brief on the trends and threats driving up risk across all tracked risk areas.
- Overview of proposed investments: at the core of your pitch, provide management with an overview of the responses needed to addressed increasing risk levels. Include a summary of the strategic impact of the various response initiatives and introduce the overall proposed investment amount, making sure to specify the difference (in percentage terms) between recurring versus new spending.
- Spotlight on investment increases: finally, provide a deep-dive into investment increases. Outline the delta of additional investment needed compared to the previous year’s budget. Wrap-up by providing a business case for each new investment increase by mapping it to its strategic impact.
Your pitch should include as few slides as possible. It should also be preceded by an executive summary with an overview of your budget request for the year.
More importantly, it should put the spotlight on investment increases as much as possible. If possible, layer all budget increases in an “incremental” way, ranking them by strategic impact. This will help your CFO and management team intuitively understand where the majority of “negotiation calories” will have to be spent.
Conclusion
Security budgeting is often neglected in cybersecurity but is a critical skill for CISOs and their teams to master. A well-prepared security budget ties funding requests to initiatives maintaining a company’s risk tolerance while demonstrating to management how security investments support overall business goals.
By aligning cybersecurity goals with business priorities, CISOs can gain management’s trust and demonstrate that every dollar spent on security is an investment in protecting and enhancing the company’s bottom line. The budget should focus on risks tracked through management reviews, tying these to tangible threat scenarios that could impact growth. Using commercial narratives to justify investments can help the board understand the importance of specific risk-reduction capabilities.
An effective cybersecurity budget also requires visual tools that present high-level overviews and detailed breakdowns of operational expenditures. Key elements include dividing mandatory from discretionary investments, mapping supply-demand dynamics for security capabilities, and categorizing budget items by their impact (imperative, strategic, or ambition-driven).
Finally, a well-designed budget tool should allow flexibility for analysis, comparison of options, and an in-depth understanding of funding requirements, ultimately enabling CISOs to pitch their budget in a structured, impactful way to the board, focusing on investment increases and strategic impact.