Free SaaS ISMS quickstart
Learn what it takes and what is needed to put together a free ISMS for SaaS companies
To carry out business, today’s SaaS organisations must demonstrate some level of compliance with internationally recognised cybersecurity standards. For SaaS companies, ISO 27001 is the certification that is most requested by customers. Obtaining such certification allows companies to demonstrate a systematic approach to information security supported by a credible commitment to employ best practices and continuously improve.
To obtain the certification companies must put in place an Information Security Management System (ISMS) conforming to the ISO 27001 standard. For SaaS companies, creating a basic ISMS should not require large investments. Knowing how to obtain ISO 27001 efficiently and an understanding of what a minimal implementation looks like is all that is required.
Obtaining ISO 27001 efficiently
Obtaining ISO 27001 efficiently requires knowing exactly where and when to spend your money during the certification process. There are three areas where a SaaS company can avoid deploying money and instead leverage existing resources:
- Writing ISMS policies: A basic ISMS can be put together by anyone with good web searching skills. The ISO 27001 standard is well documented online with plenty of free resources. Additionally, AI chatbots such as Gemini or ChatGPT can accelerate the process. However, these must be used correctly and with an understanding of their limitations when it comes to generating ISO 27001 policies.
- ISO 27001 consulting: While dedicated ISO 27001 consulting can also help accelerate the process of building and writing ISMS policies, for most SaaS companies it is often an unnecessary expense. For most SaaS companies, an initial ISO 27001 certification can be scoped to only cover the SaaS product offered to customers. There is no need, at least initially, for an ISMS that covers the entire company. ISO 27001 consulting may be worth considering only when the scope of the ISO 27001 certification needs to cover the whole company. However, consulting services may be justified in cases where SaaS companies are operating complex products spanning multiple platforms and jurisdictions.
- GRC tooling: While governance, compliance and risk (GRC) management tooling provides numerous benefits, it is not needed during the initial build phase. With costs typically starting north of 30K USD per year, tooling makes sense only when your company is looking to scale GRC activities across the entire company.
While the above can help you save some of your budget, there are other areas where you cannot avoid spending money, these are:
- Investing the time of a dedicated resource: Even if using AI tools or off-the-shelf policies, you will still need to allocate a full-time resource to build the initial ISMS. The overall ISMS building effort will be ultimately determined by the size of the company and product complexity. However, for most SaaS companies, developing a basic ISMS should take no more than four months (assuming a SaaS company of circa 120 employees operating one product). Still, you will have to pay the salary and time investment of a dedicated resource for those 4 months.
- Paying for external certification: Once you have your basic ISMS in place, you’ll need to pay an external auditor to review your ISMS and certify your company. While the ISO 27001 certificate will ultimately unlock thousands (if not millions) of dollars worth of new business, you must pay the upfront certification costs.
- Budgeting for running costs: Once certified, you must maintain your certification. The ISO 27001 certification demands regular internal and external inspections of the ISMS to ensure the company follows the underlying policies. These inspections will result in recurring costs. Finally, to actively maintain your ISMS and ensure audit readiness, you’ll probably have to hire a dedicated specialist.
As you can see, an ISO 27001 certification cannot be obtained entirely for free. However, by knowing where it makes sense to spend money, SaaS companies can make sure capital is allocated efficiently during the certification journey.
Minimal implementation requirements
A minimal ISMS implementation rests on three pillars: the certification scope, the core policies and the minimal set of tools and processes needed to operationalise your ISMS. Each of these three pillars plays a fundamental part in gaining an ISO 27001 certification. We’ll now examine each in turn.
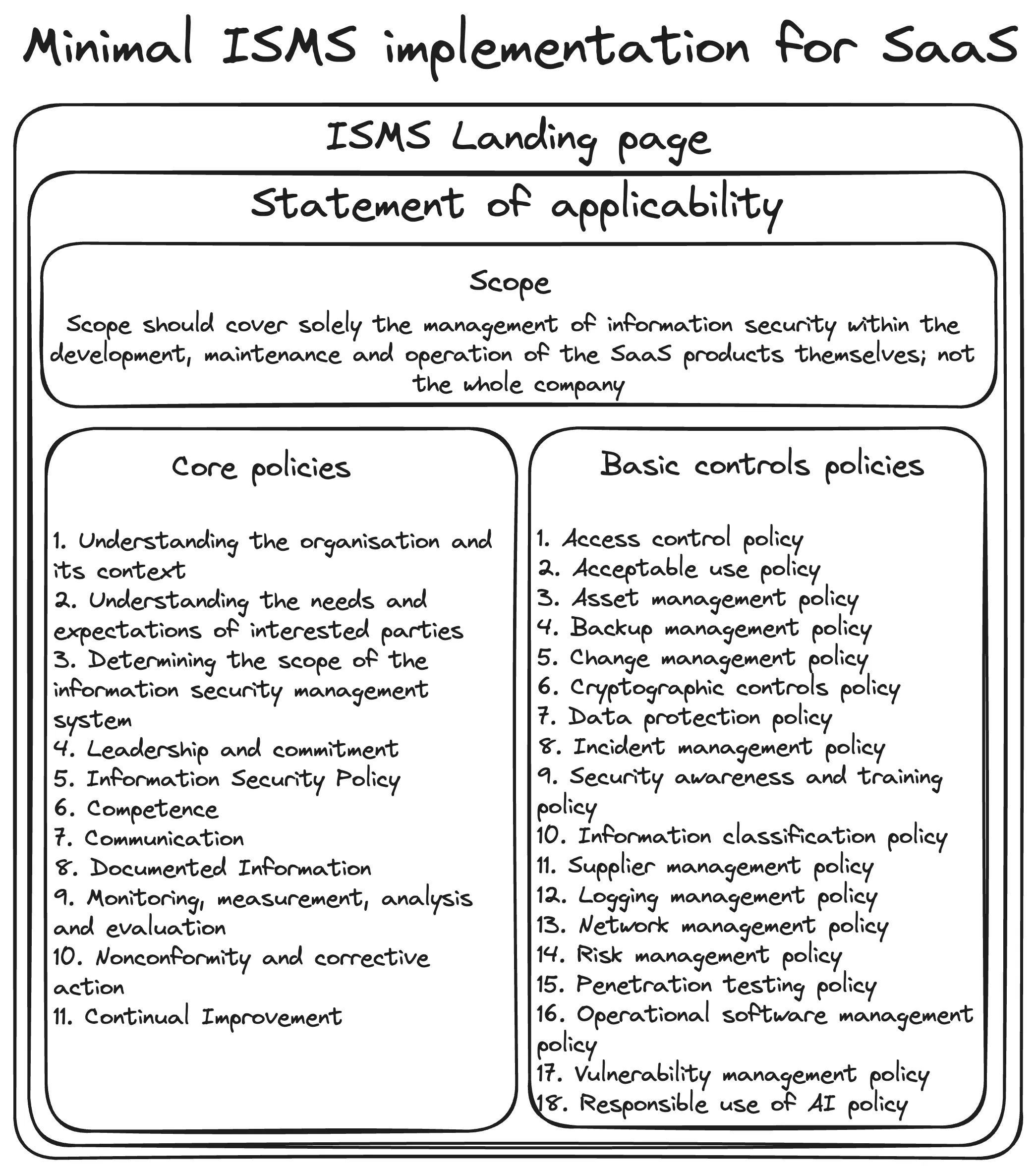
Certification scope
The ISO 27001 standard grants a certain degree of freedom in defining the scope of a company’s certification. Specifically, the standard grants the freedom to specify which areas of the business are covered by ISMS controls, and which are not. SaaS companies looking to obtain certification can leverage this flexibility to define a minimal scope that is efficient to implement.
Typically for SaaS companies, such scope should cover solely the management of information security within the development, maintenance and operation of the SaaS products themselves; not the whole company. This sustainably reduces the amount of policies, tools and processes that are needed for a minimal ISMS implementation, without compromising the ability to obtain the certification.
In a restricted ISMS scope some company assets and information would inevitably fall outside the ISO 27001 certification. However, this would not automatically imply that such assets would no longer be subject to security measures. With a restricted scope, you can transfer the implementation responsibility for security measures applicable to out-of-scope assets directly to the persons responsible for managing those assets. All you have to do is to make this fact clear within your policies.
Core policies
The ISO 27001 standard lists all the requirements to establish, implement, maintain and continually improve an ISMS. By following such requirements, companies can develop an ISMS that preserves the confidentiality, integrity and availability of company information. Through the ISMS, companies can demonstrate that they apply the right processes to identify and manage information risks.
To obtain ISO 27001 certification, SaaS companies must adapt such requirements to their organisation’s needs and operating reality. Once adapted, the requirements can be crystallised within eleven core ISMS policies. These are:
- Understanding the organisation and its context
- Understanding the needs and expectations of interested parties
- Determining the scope of the information security management system
- Leadership and commitment
- Information Security Policy
- Competence
- Communication
- Documented Information
- Monitoring, measurement, analysis and evaluation
- Nonconformity and corrective action
- Continual Improvement
All the above policies must be written and documented for the core ISMS to be established.
Basic controls policies
The ISO 27001 core policies on their own will not be sufficient to obtain an ISO 27001 certification. The core policies will outline how your SaaS company has built an ISMS to suit its information security needs and how it helps manage risks over time. However, in addition to the core policies, you must also write and document the necessary control policies that outline how your company manages the risks identified through the ISMS.
Fortunately, the ISO organisation also provides the ISO 27002 standard which provides a reference list of all the possible controls that can be selected to manage risks identified through the ISMS. The list contains more than 90 controls, making it quite daunting for a SaaS company to decide which controls are applicable and which are not. Fortunately, a minimal SaaS ISMS does not require a policy to be written for each control. While there will be variations between companies, most SaaS companies can get away with defining the below control policies:
- Access control policy
- Acceptable use policy
- Asset management policy
- Backup management policy
- Change management policy
- Cryptographic controls policy
- Data protection policy
- Incident management policy
- Security awareness and training policy
- Information classification policy
- Supplier management policy
- Logging management policy
- Network management policy
- Risk management policy
- Penetration testing policy
- Operational software management policy
- Vulnerability management policy
- Responsible use of AI policy
For most SaaS companies, the above list of policies should be sufficient to cover the vast majority of ISO 27002 controls. Over time, you may expand the list to adapt it to business and operational changes. As a start, the above should be sufficient to get a SaaS company certified.
Statement of applicability and landing page
To wrap up your ISO 27001 writing efforts, there are two additional documents needed: a statement of applicability and ISMS landing page.
A statement of applicability (SoA) is a key document to achieve ISO 27001 certification. It details which of the recommended controls from the standard your organisation implemented to manage information security risks. The SoA also explains why you selected these controls, along with any controls you decided not to implement and the justification for their exclusion. This helps auditors understand your approach to information security and ensures your ISMS is tailored to your company’s needs.
The ISMS landing page instead brings together all of your ISMS policies into a single, convenient place. It can be used to educate employees about information security, communicate the organisation’s commitment to information security, and demonstrate that the organisation is meeting the requirements of ISO 27001. Finally, it can also be used by auditors to access information security documentation during audits.
Creating a good landing page is not complicated. There are a few simple building blocks needed and the trick is to know what ISMS pages need to be included within the different sections of the landing page.
Tools and processes
Once your policies are written, indexed on your landing page and listed in your SoA you will have an ISMS. However, the work does not end there. To operationalise your ISMS you’ll need some dedicated tools and processes to tie everything together. The picture below provides an overview of the tools and processes needed as well as how they work together to support an ISMS:
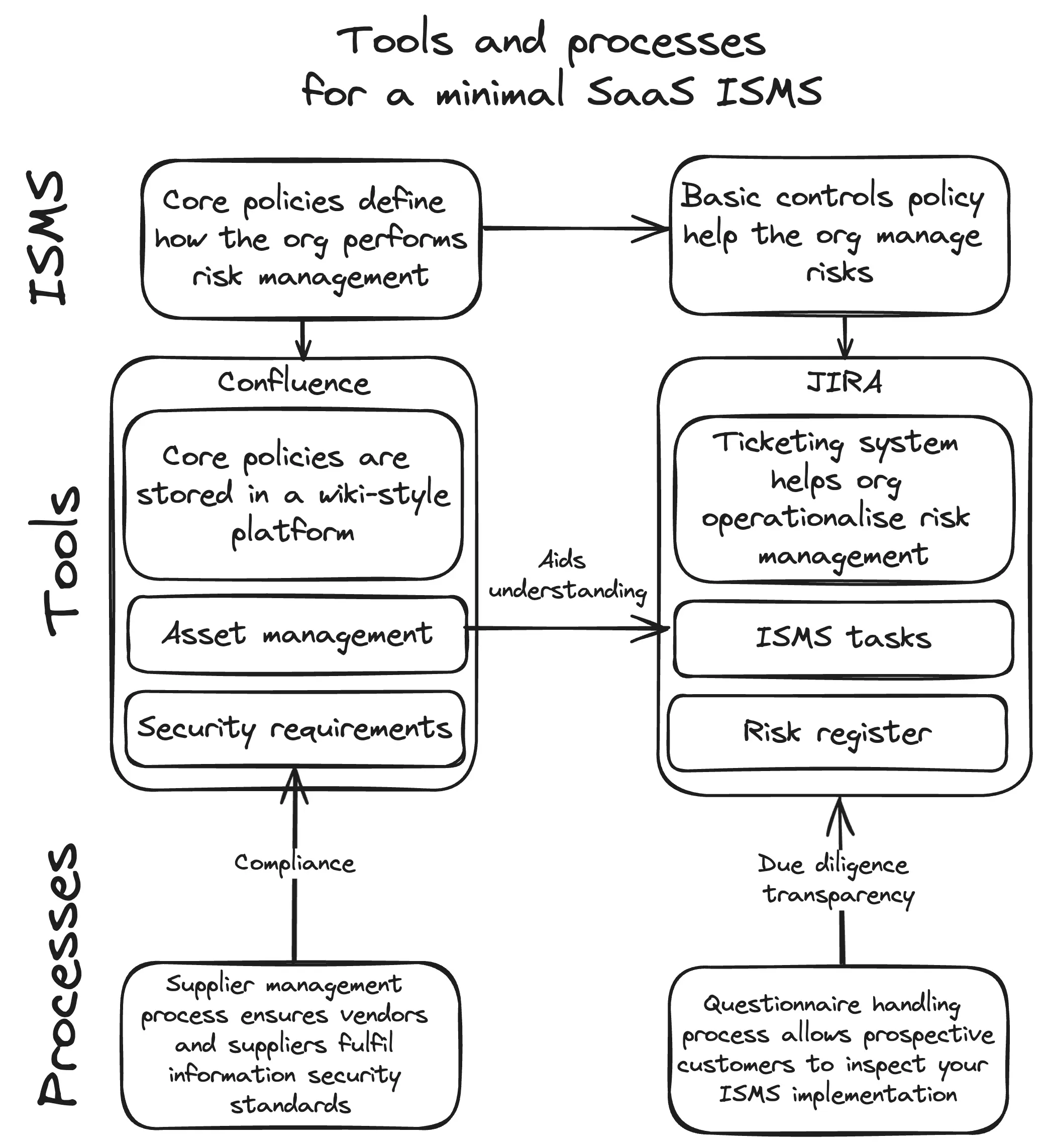
To expand on the above picture, the minimal tools and processes needed are as follows:
- Content storage: To document your ISMS you’ll need content storage. Typically, a wiki-style platform (such as Atlassian Confluence) will be ideal. It will allow you to store your documentation and manage the distribution and accessibility of the policies across your company. If you are pressed for costs you do not necessarily need to store your ISMS on a wiki-style platform. Even simply storing Word documents on GDrive will be sufficient. What matters is that the documents can be accessed by company employees and that only authorised personnel can change them.
- Ticketing system: To operationalise your ISMS and execute on your chosen controls you’ll need a ticketing system. Atlassian JIRA is a convenient platform to use in this context. It can be configured to create recurring tasks. This is helpful when you need tickets that regularly remind you to check the correct execution of ISMS controls. Additionally, JIRA also offers several plugins that can simplify the maintenance of an ISMS. For example, Risk Register for JIRA can be freely installed to create JIRA projects that are pre-configured to act as an ISMS risk register.
- Asset management: To obtain certification, you must pair your ISMS with a capable asset management tool. You won’t be able to run your ISMS without understanding the tangible and intangible assets used every day by your company. In general, device management software will not be enough to obtain certification, a dedicated asset management tool is needed. You can purchase dedicated asset management SaaS platforms. This will be more expensive but will significantly speed up implementation efforts. Alternatively, a basic but capable asset management tool can be created with Excel.
- Supplier management process: Information risk management does not stop at your company’s doorstep. Having an ISMS also means you’ll need to ensure you are working with vendors and suppliers that fulfil your information security standards. A supplier management process helps with this. Such a process will help you identify suppliers that can operate within the bounds of your company’s risk tolerance. Fortunately, tools such as AI chatbots can also help to accelerate supplier risk assessments.
- Questionnaire management process: Once you’ve obtained ISO 27001 certification, prospective customers will likely want to inspect your ISMS implementation. While some customers will trust your certification at face value, many regulated (or large-sized) companies will still want to ensure that your company follows its policies. To this end, they’ll typically send over a security questionnaire for your team to complete. Without a questionnaire handling process, these requests can quickly become cumbersome and interfere with your team’s day-to-day activities
The above list includes the most basic tools and processes needed to operationalise an ISMS. However, the list is not exhaustive and may be extended to include additional tooling to fulfil other, more specific ISMS controls. For example, if you decide to implement a vulnerability management policy, you’ll likely need to purchase vulnerability management software to operationalise the policy.
Conclusion
Obtaining ISO 27001 certification will demonstrate a systematic approach to information security for your SaaS company. Additionally, it will open the doors to business opportunities with larger and more regulated companies. While there are some upfront costs, there are also clever ways to save money.
Costs can be saved by intelligently picking a reduced scope, leveraging existing resources and reducing the use of consultants or specialised tooling. However, the certification process will not be entirely free. Writing, certifying and running an ISO 27001 ISMS will require some inevitable investment.
However, by focusing on efficiency and a minimal implementation, SaaS companies can obtain ISO 27001 compliance with as little capital as possible. Once the certification attracts new business from larger companies, the low capital investments should be rapidly recouped.
