Help I'm a new CISO! Tips to make a great impression on probation
Have you managed to land your first CISO role? Great, now you need to quickly impress! Find out exactly how it's done

Have you managed to land your first CISO role and are about to start? First off, congratulations on getting the job. With the demand for senior security roles being at an all time high, beating the competition to secure such positions is a huge challenge. So well done you! You’re awesome!
However, with increased seniority comes increased responsibility. As a new CISO, making a great first impression is crucial to laying a solid foundation for your tenure. Your management will have already waded through hundreds of applications to select you. As a result, they will be keen to see what you can bring to the game.
More soberingly you will have joined a division which is a cost to the company, bringing no money to your employer. Moreover, your salary will probably be one of the major cost items (excluding technology costs) within the company’s security budget. As you can imagine, you will need to show value faster and more creatively than peers working within company profit centres.
If you landed such a role you most likely understand these challenges better than everyone else. However, as a new CISO, it can be daunting to walk into one of the most high-pressure roles in cybersecurity without some sort of guidance. Fortunately, there are a couple of things that you can do to set yourself (and your team) up for success.
Fine-tune your probation goals by the third week
Given the highly dynamic nature of cybersecurity (and depending on the size and nature of the company you’ll be joining) you’ll probably hit the ground running. You’ll find yourself having to manage incidents, address security risks to the company and deal with a different way of doing things. You’ll have to do all of this while taking over from your predecessor and getting to meet your new teams.
Very quickly you’ll find yourself swamped with competing priorities and getting lost in day-to-day management. In such a situation, it is easy to lose sight of your probation goals and for mis-alignments to open up with your managers. To avoid this situation you must re-align your probation goals rapidly and aggressively. Ideally, you should do this in your first 3 to 4 weeks of employment. Moreover, you should do this regardless if you have been provided (or not) a set of probation goals at the start of your new job.
Probation goals are rarely defined by people who fully understand the challenges of your job. Because of this, you’ll save yourself some surprises down the road if you review and re-calibrate them in your first weeks of employment. You won’t be able to fine-tune or change all of them. However, you’ll be able to exert some influence over them and increase your chances of success once probation comes to an end. More importantly, you will showcase excellent self-direction skills and a willingness to understand what matters most to your new employers.
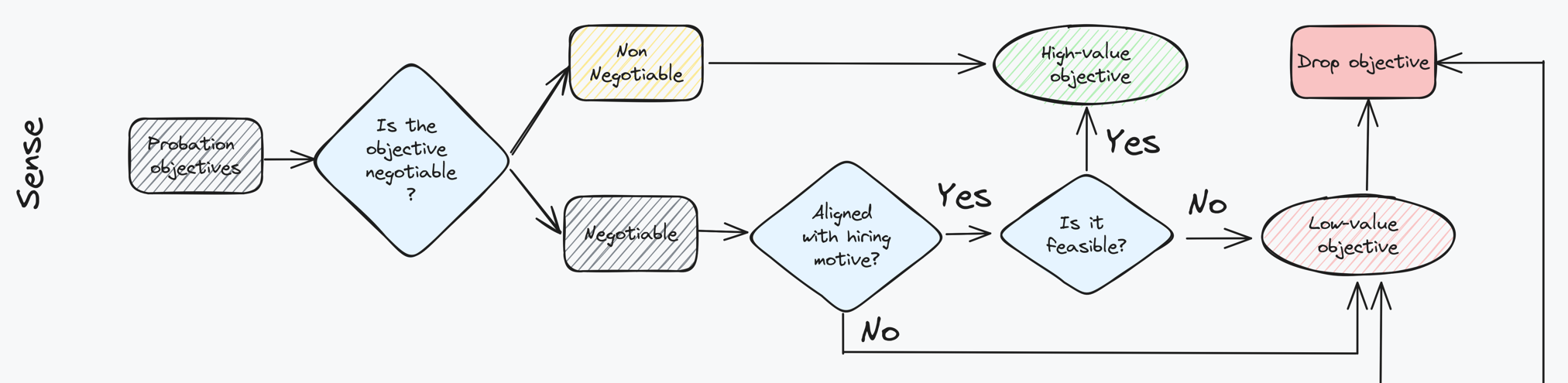
You will have to drive the review, your managers won’t do it for you. To do this, in the first few weeks of employment you should carefully review your probation objectives and identify the following:
- Non-negotiable objectives that you must meet. These will typically be made clear to you when starting. Identifying these will help you discriminate between goals you will be able to influence and goals you won’t
- Negotiable objectives that could be changed. These can include objectives that feel extracted from a standardised list or that are not specific to cybersecurity, your job or to the business
Once you have identified negotiable objectives you should work to understand which ones deliver limited value. Even better, you should pick ones that, in your view, cannot be delivered based on the early observations you have made about existing team projects or workloads. Your goal should be to entirely eliminate these objectives. Alternatively, you should try to swap them for higher value-add objectives (more on that later).
You should then review your non-negotiable objectives and assess them against the main hiring motives that were given to you during the interview process. During such process you will have been made aware of the reasons why the company decided to change CISO (or hire one). Such motives could range from poor performance or lack of competence from your predecessor. Even commercial needs, such as lowering security costs or migrating to the cloud, might also have driven the decision.
Regardless of the precise reason, you must work to understand the need that drove your recruitment. Based on that, you should compare these reasons against all your probation goals to ensure that they all prove, in some way, that you were the right choice. If this is not the case, then you must work to understand a) why was the goal established by management in the first case and, b) how can it be improved to better align to the business needs that led to your selection.
Once you have reviewed your goals, schedule an alignment meeting with your manager and be explicit about the need to ensure probation goals are aligned with the company’s (and your manager’s) needs.
Meet your teams over SWOT sessions
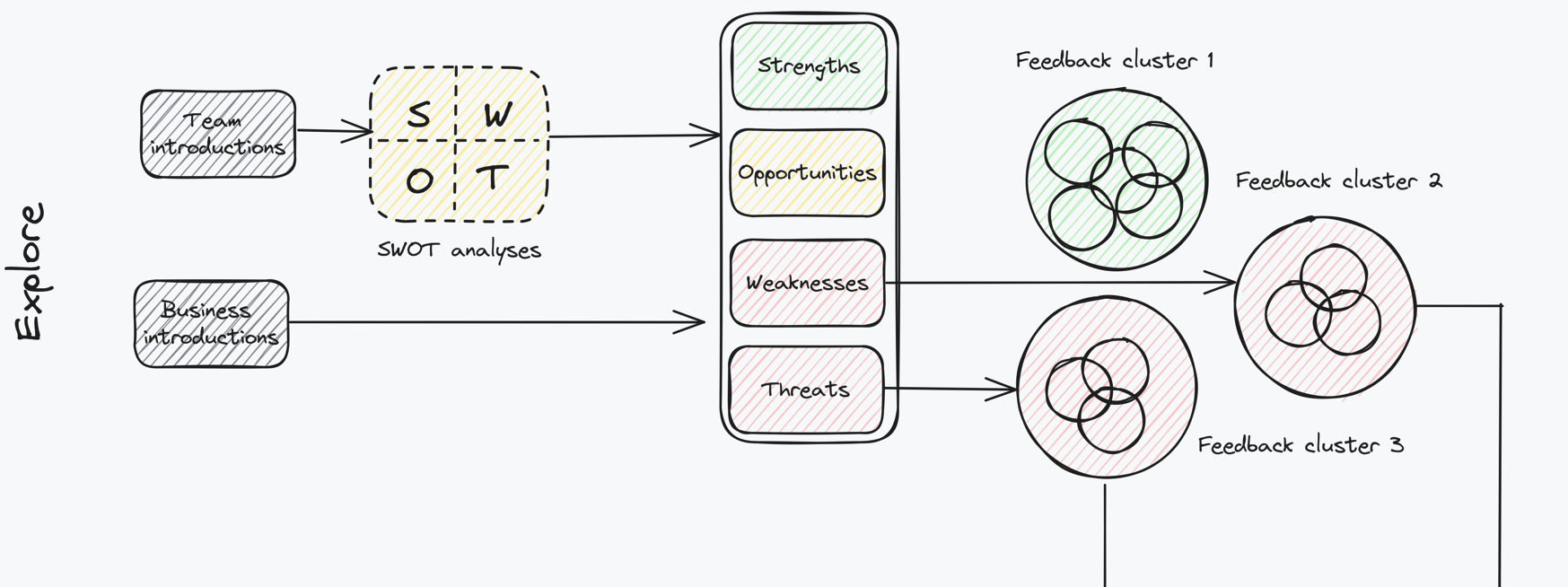
During the first months you should build a rough picture of what works, what doesn’t and what can be improved. Moreover, you should do so in an efficient and methodical manner. A great solution can be found in introductory team meetings: as you get onboarded into the firm you will have to attend introductory meeting rounds with your teams.
Such meetings offer an excellent opportunity for you to learn what are the top concerns for your colleagues. In order to stimulate such conversations you should ask team leads to prepare short SWOT analyses of ongoing teams and operations.
A SWOT analysis is a strategic planning tool used by businesses and individual teams to identify and assess their internal strengths and weaknesses, as well as external opportunities and threats. The acronym “SWOT” stands for:
- Strengths: These are internal positive attributes or resources that give a team unique capabilities.
- Weaknesses: Internal factors that place a team at a disadvantage or hinder its ability to achieve objectives.
- Opportunities: External factors in the environment that the team could potentially exploit to its advantage.
- Threats: External elements that could negatively impact the team’s performance or pose risks to its success.
When asking your teams to prepare such analyses, take care to frame your request appropriately. You should avoid giving the impression that you are attempting to find low-performance teams or scapegoats. The people meeting you will be very eager to shake hands, but also quite nervous. A poorly formulated request asking for SWOT analyses can quickly lead to suspicions and second guessing of your true motives.
To avoid this situation you should be clear and forthcoming with your new colleagues: explain to them that the request for SWOT analyses is to help you find areas of immediate improvement or areas where you can potentially provide your input, expertise and support. You should make clear that the goal is to get to know each other while setting in motion habits that promote feedback sharing and continuous improvement.
While it may be difficult for most teams to be completely open with you on their first meeting, you’ll be surprised at the amount of insights you’ll get and how willing your colleagues will be to share their concerns. While some of the shared materials and concerns might be “curated”, most inputs will prove valuable in sensing what works well and what doesn’t.
Finally, make sure to provide a clear agenda and structure to your introductory meetings. Before scheduling the meetings make sure to send communications to all teams explaining the aim of the sessions. Put emphasis on the need to get to know each other and what are the top security priorities. Use the meeting agendas as a second opportunity to explain the goal of the sessions and to allocate 1/3 of the meeting time for colleagues to introduce themselves. The rest of the meeting time should be allocated to the SWOT sessions, giving you ample time to ask questions and dig deeper on the feedback if needed.
Try to formulate agenda items as open questions rather than as a task list (for example, where do we see the biggest opportunities for your team? vs team opportunities discussion) and use inclusive, gregarious language throughout the agenda. Arrive on time and actively listen. Try to speak the least (and restrict it mostly to your introduction at the start of the meeting) and limit yourself to asking questions.
Understand where security can make an impact
In parallel to running your SWOT sessions, you should also schedule introductory meetings with peers and directors on the commercial side of the business. Besides giving you the opportunity to show your face, such sessions are a great platform to deepen your understanding of the business.
During these sessions you should ask your business peers to describe what are the firm’s top 3 revenue generating streams. By the third or fourth introductory meeting you will have gathered a sense of what these top 3 revenue streams are and can begin iterating and refining your knowledge with each new session. Rather than just getting a general understanding, you should strive to make a genuine effort in understanding what brings money to the company. If your peers allow it, you should ask for access to further documentation that can help you further understand the company’s main revenue streams.
While deep-diving into the company’s revenue streams you should concentrate on understanding the processes and, more importantly, identifying the technologies that support such processes. As you progress in your research you should begin clustering the different technologies that you have identified and validate them with any available technical documentation that your team has access to (i.e. asset inventories, crown jewel databases etc.).
Finally, once you’ve understood what the revenue streams are and the technologies supporting them, you should ask business peers to share feedback regarding their perception of security within the organisation. In particular, you should ask three questions:
- Is there anything that the security team should start doing to support your processes or secure your technologies?
- Is there anything that the security team does that produces pain points for your team and processes?
- Is there anything that the security team is doing particularly well in supporting or protecting your processes?
Hopefully, these three questions will yield feedback and guidance to help you identify business areas where security improvements can make a big impact. Moreover, your inquisitive behaviour should have helped form a positive impression on your business peers. By meeting a CISO that actively looks to understand how the business works, they’ll probably be reassured in having met a security leader that includes a deep understanding of the business in the firm’s risk management approach.
Once you are halfway through your introductory sessions (both with your teams and business leaders) and have gathered sufficient feedback you should start quickly connecting the dots. Your goal, at this point, should be to:
- Cluster security weaknesses, threats and opportunities and identify the most common ones
- Out of the most common security improvements, identify (with your team) any potential quick wins that are achievable in one or two quarter
- Match security quick wins bringing the most impact with the top revenue generating business processes or technologies
Once done, you should aggressively validate your analysis and conclusion with both your teams and business peers. This initial validation is extremely important to ensure you have truly identified areas of improvement that will bring tangible impact to the business.
Considering your short tenure in the company, you may be identifying the wrong areas of improvement or going down the completely wrong path. Before you pitch your ideas in front of a larger audience or your managers, you should test your ideas in the safety of 1-to-1 conversations with business peers and teams. Be humble when validating your ideas and be prepared to acknowledge your mistakes, listen attentively and adjust accordingly.
Kick-off urgent security initiatives
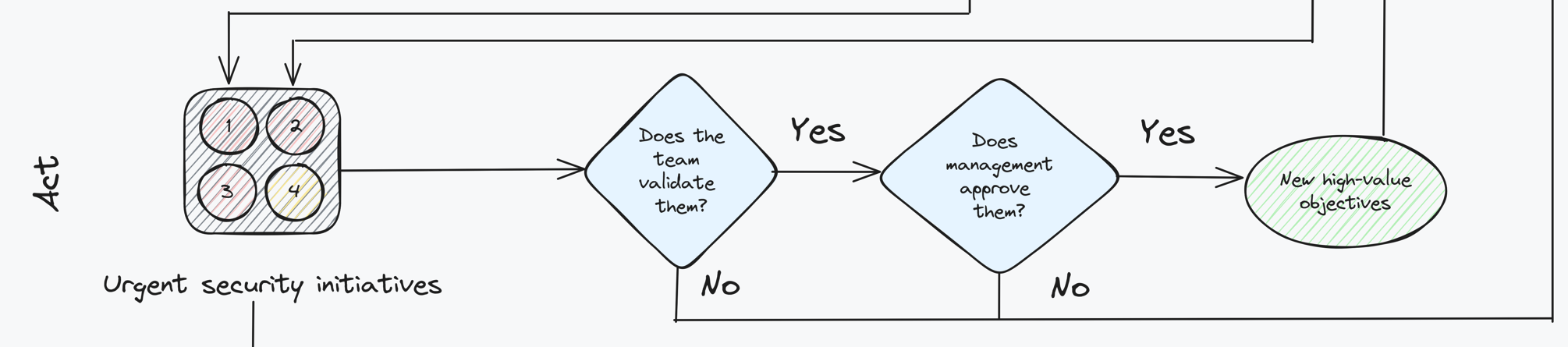
Once you have validated your ideas you should create a small roadmap of urgent security initiatives to be launched as soon as possible. The roadmap should contain no more than 8 security initiatives. Each should aim to close urgent security gaps that bring tangible improvements to the business within a maximum of one or two quarters. With this roadmap your goal should be to strengthen your company’s security posture rapidly, tangibly and by leveraging “quick-wins”.
The roadmap should be defined in a simple document that you can quickly share with your teams and management for approval. One-pagers are the ideal format here, preferably one slide power points. The idea is that this document should be self-contained and outline all the information needed to successfully pitch your security initiatives to a wider audience. Avoid long presentations and complex documents: the key is to get approval, kick-off these initiatives and generate value add as fast as possible. A short brief that gets to the point is ideal in this case.
An effective one-pager that promotes rapid decision making should, at a minimum, contain a table with the below columns:
- Risk area: this column should outline the business area or, better, the business process or product that is currently carrying the information security risk and that will be tangibly improved by the proposed initiative
- Proposed initiative: this column should outline, in the most compact format possible, what exactly your security team is going to fix. Avoid explaining why the fix is needed. Just outline the fix in the shortest form possible. A good example could be: “Upgrade tool X subscription from Pro to Business”
- Rationale: in this section you should explain, in a compact manner, the tangible benefits that the initiative will bring. This is the column where you insert your elevator pitch, so focus exclusively on the value-add of the initiative, a good example could be: “Fully protect platform Y against credential leak/theft attacks”
- Management support needed: this is also a key column. Here you have the opportunity to explain the exact type of support you need from management. Be specific and use categories to immediately communicate the type of support that management needs to give you (besides approval and endorsement) for the initiative to have success. Some example categories could be: “Financial support”, “Communications support”, “Re-prioritisation and delegation to relevant teams”, “OKR change for team Z”
- Status or ticket (if available): this is an optional column. However, considering your managers and teams will become familiar with it, you could use the same one-pager as a means to track initiative status and completion. For example, you could copy paste the slide in Confluence, link relevant Jira tickets and then track progress accordingly
Once you have successfully launched your initiatives you will have demonstrated both to management and your team a number of excellent attributes. For example, by identifying areas of immediate improvement, you will have demonstrated great capacity for synthesis and recognising where security can collaborate with business to bring impactful change. Secondly, by gathering the necessary consensus and approvals, you will have demonstrated leadership skills and the ability to quickly take charge of your domain.
Want the slide? Then subscribe to Premium and download the compact one pager to get your security initiatives approved fast!
Rally your team and deliver
Your newly launched initiatives will need to be delivered rapidly and within a short time span. For the initiatives to be delivered successfully, you’ll need to rally your team and get to work alongside them. Hopefully, the fact that you have involved some of your teams in validating the security initiatives should already have given you the chance to collaborate and professionally “sense-check” each other.
However, to start rallying together your entire division (and not just the teams involved in the urgent security initiatives) you can start doing a couple of things.
First you should begin establishing a tone and high-level vision outlining the ethos your security teams should embrace. Ethos and values are hugely important in fuelling a sense of mission and purpose and your teams will be grateful to get a sense of what principles you’d like to establish during your tenure. They will guide your team in understanding WHAT are the right approaches to adopt in their day-to-day work.
Here there are two low-effort things you can do to get the ball-rolling:
- Promote a “no broken windows” attitude: this attitude or policy, derived from the broken windows theory in criminology, emphasises the importance of maintaining order and addressing minor issues promptly to prevent the escalation of more significant problems. It suggests that visible signs of disorder or neglect (in a manner similar to broken windows, graffiti, or litter) in a company’s security stance can lead to an increase in security issues down the road. By proactively addressing and fixing these small issues, your security team can create an environment that encourages security rigour and hygiene and fosters a sense of safety and security. By encouraging a “no broken windows” attitude, you’ll plant the seeds for a working environment where speaking up is the norm and things get fixed
- AMP up your team’s motivation: establish simple but clear expectations of what approaches your team should follow when working. To get your colleagues to really care about what they do in their day-to-day job, avoid any kind of stick and carrot methods and embrace a culture of motivation by promoting, for example, the AMP model. This model, popularised by author Daniel Pink, outlines three key motivators essential for fostering engagement and satisfaction in work. Autonomy, mastery and purpose. Autonomy refers to the desire to have control over one’s work and decisions, allowing individuals the freedom to direct their efforts. Mastery involves the pursuit of continuous improvement and the development of skills in a particular domain. Lastly, purpose encompasses the sense of working towards something meaningful and beyond oneself. When these elements are present in the workplace, individuals tend to be more motivated, productive, and satisfied, leading to increased creativity, higher job performance, and a deeper sense of fulfilment in their work. By embedding such a model in your division, you’ll be promoting a more empowered and fulfilled workforce, contributing to overall productivity and organisational success.
Secondly, you should outline HOW you expect your team to operate in day to day work. Again, acronyms and soundbites are also an excellent tool here. For example, a useful acronym that can be used to communicate principles to adopt in the workplace is “Triple A” or “AAA security operations”.
Historically, triple A is associated with a security framework that controls access to computer resources via the principles of authentication, authorization and accounting. Lately, in the context of security operations, triple A has started to embody the idea of embedding analytics, automation and artificial intelligence in all aspects of the work done by security teams.
Regardless, triple A is a good example of using acronyms to communicate key operational principles to larger audiences. You could use the same acronym to build your own version. One good example is using triple A to encourage security teams to embed the principles of Automation, Asynchronous workflows and Auditability in everything they do. The goal here is to give your teams a north star to follow when building processes, implementing technologies or proposing new work streams. By communicating operational principles in such a compact manner, your security teams will always have the necessary tools to distinguish between improvement suggestions that bring value versus those that do not.
Once you have established the ethos and operational principles for your team, you should then make an effort to over communicate them using every single opportunity granted to you. From company newsletters, to town halls all the way to the smallest meetings. You should remind your teams of the ethos and principles they can use to govern their decision making during their day-to-day.
To conclude, while your first months as a CISO will be some of the most challenging, by employing some simple rules and strategies you can increase your chances of making a great impression from the get go. Doing so will give your employers a signal that they made the right investment in hiring you. To your colleagues and teams, this will provide tangible signs of the workplace culture you’d like to promote. More importantly, they’ll get a sneak-peek into how you drive, prioritise and roadmap security initiatives for the benefit of the division and the business. By doing all of this, you’ll be setting yourself and your teams for longer term success.
Combined, all the above tips and tricks come together to shape a neat CISO objective setting playbook for those crucial probation months:
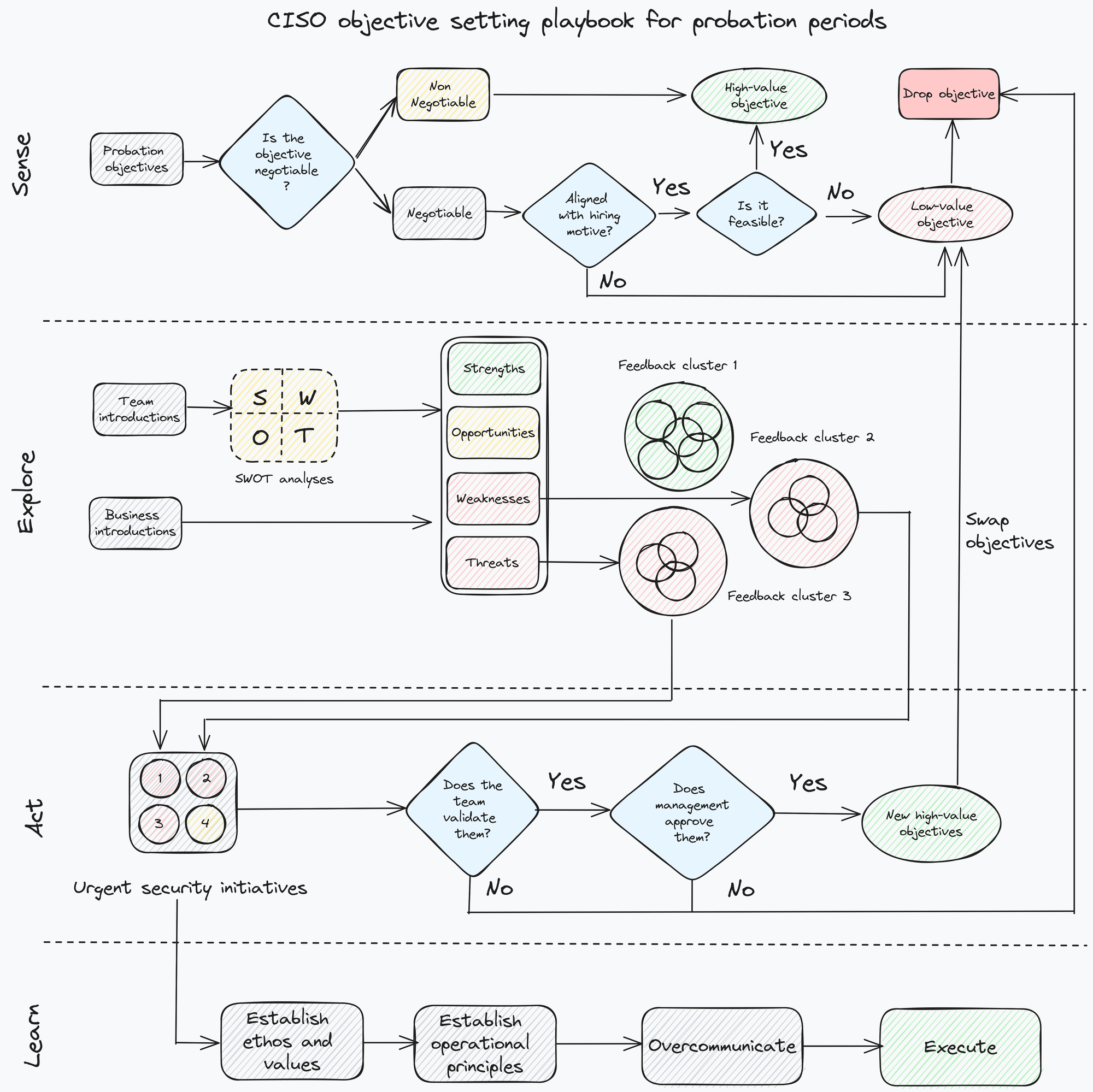
Use and adapt this playbook to your needs and as you see fit. Wether you are a CISO or a senior security manager (or, in fact, a security professional regardless of position), it will hopefully help you build a path to success during those precious first months on the job. Best of luck!