Running lean management reviews
Get leadership's full attention with lean cybersecurity management reviews that respect everyone's time

Running effective cybersecurity management reviews is hard. Executing them in a manner that gets leadership’s full attention while respecting everyone’s time is even harder. Management reviews are a crucial tool to bridge the gap between business and security leaders. Do them right and you have a fair shake at building a robust cybersecurity program. Mess them up and management will be having the wrong conversations about cybersecurity.
More importantly, management reviews can be one of the most impactful tools for security leaders. It is true that on a formal level, they are an unavoidable requirement of standards such as ISO 27001. However, on a softer level, they can be an effective tool to shine visibility on the activity of the security team, quantifying their impact.
Crucially, they help secure backing and funding for key security initiatives, helping set the direction and empowering security leadership. These reviews are the primary platform to communicate the value of security investments and justify resource allocation.
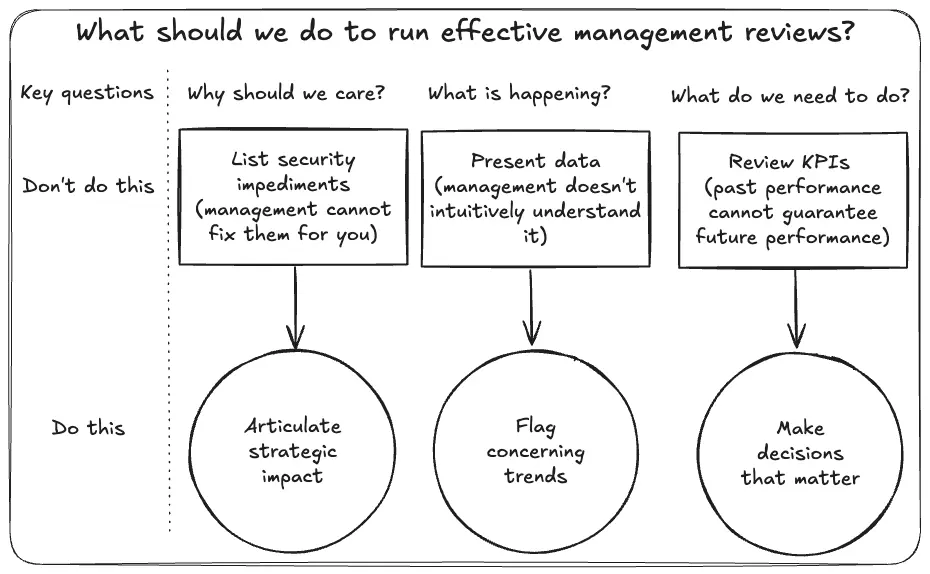
Why running effective management reviews is hard
Running effective management reviews presents several challenges. First, they must effectively distil security impediments into strategic imperatives, bridging the gap between security leaders and business decision-makers. This requires translating complex technical details into clear business risks and opportunities.
Secondly, they need to promote decision-making rather than formal, rigid reviews of past performance (a format which, ironically, is largely encouraged by the ISO standard itself). Boardrooms and executive teams are tasked with making strategic decisions. It is by harnessing this strength that security leaders can avoid paralysis and ensure their work is frequently inspected and approved. This means adapting the review process to harness the power of executive decision-making.
Finally, trends are needed over Key Performance Indicators (KPIs), metrics, and data. Trends help flag areas of concern and stimulate discussion about possible causes. In turn, hypotheses can lead to defining response options that can be debated and weighted before execution. Simply presenting raw data to determine if KPIs are being met, without context or analysis, is ineffective.
The solution: lean management reviews
Lean management reviews tap into a few simple ideas. When the audience is unfamiliar with cybersecurity, the chances of securing backing and funding are higher if meetings are short, on-time, efficient, and geared towards decision-making. By employing meeting management best practices, we ensure that a) the right stakeholders are involved; b) they are properly briefed, and c) they are empowered to make decisions.
The goal is to have stakeholders make strategic and spending decisions that propel your team into action, not just review your team’s performance. The net effect is to prevent your boardroom and management team from having the wrong conversations about cybersecurity, with unpredictable effects on your security program. Lean management reviews abandon the concept of formal, stilted, and rigid management reviews: reviews happen every quarter and provide an overview of the main trends in risk management, across all risk areas rather than an over-emphasis on formal governance and compliance.
Meeting efficiency helps increase executive productivity, whose time is expensive for the company. This makes the security team not only effective in communicating security risks but also puts them at the forefront of combating meeting inefficiency, which can cost big companies over USD 100 million a year.
Lean management reviews focus on risk trends that demand immediate attention, not solely on whether KPIs are being met. This allows for rapid problem identification and taking decisions immediately after, or right before, problems become more complex and expensive to remediate. This format drives agility, proper management oversight, and alignment between business and security leadership.
A concrete example: SaaS lean management reviews
Take the example of a SaaS company of 150-200 employees who onboard customer’s data and, consequently, customer threats. Let’s also assume that, for auditing purposes, the requirements of the ISO 27001 standard need to be respected. These requirements are well defined in the standard and dictate that in each review the management team must look at.
For example, the requirements include reviewing the status of actions from previous management reviews; changes in external and internal issues that are relevant to the information security management system (ISMS) or trends in nonconformities and corrective actions; and many more.
In this context, a lean management review could take place every quarter. Following meeting best practices a management review report is circulated to the company’s executive team at least two weeks before the review. The meeting takes place once every executive has had the opportunity to read the report. The report should be short, containing no more than 6 or 7 pages. Finally, the report should be structured as follows:
- Executive Summary Section: This section starts with key results achieved in the quarter and includes the status of actions from previous management reviews. It then covers upcoming challenges observed in trends and lists the key risks that management (in concert with the security team) must tackle. This section aims to ensure that management quickly grasps the main wins from the past quarter and the main decisions that will have to be taken during the review.
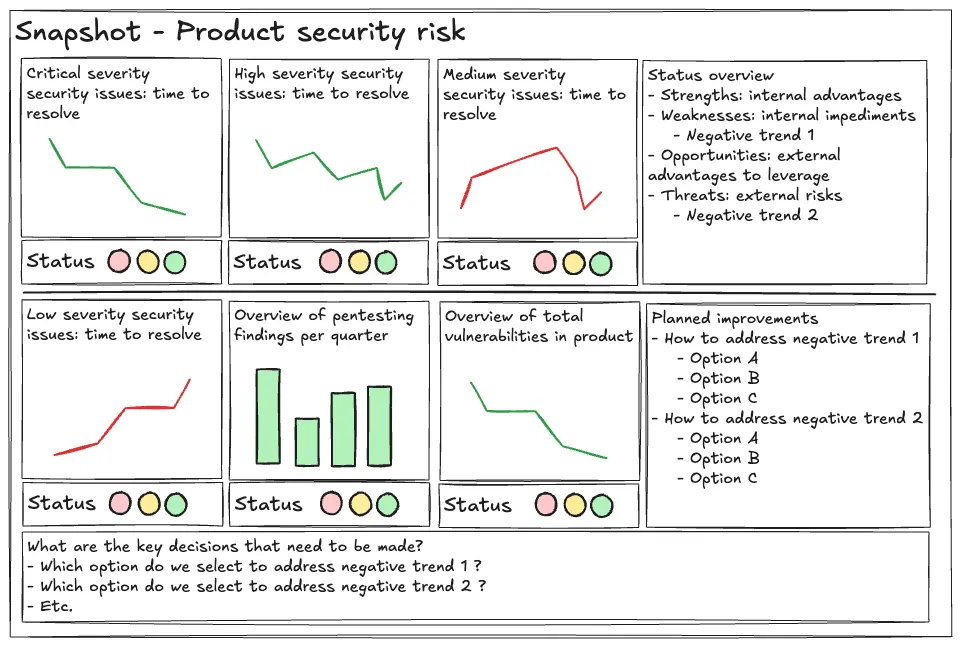
- Product Security Risk Section: Here, management can understand how quality and security controls are consistently being applied across company products. At a minimum, we must include data-driven trends on metrics such as time to resolve critical security issues across severity categories (i.e. Critical, High, Medium, Low, etc.); the number and frequency of pentesting findings per quarter; and the number and frequency of total vulnerabilities in the product, with trendlines covering infrastructure, backend, and software dependencies. By doing so, we address several ISO 27001 requirements such as reviewing trends in monitoring and measurement results, trends in information security objectives, feedback from interested parties and opportunities for continual improvement.
- Company Security Risk Section: This section allows management to review the latest threats against the company. Additionally, it helps assess the impact of security awareness training programmes. Consequently, this section must include data-driven trends on security training completion rates; phishing and spear-phishing response rates; the trend of vulnerabilities in company assets (such as laptops and excluding product assets); the trend in numbers and types of security incidents; and an overview of phishing attack types (specifically calling out AI-augmented attacks).
- Audit and Compliance Risk Section: This section enables management to retain situational awareness of audit, legal, and compliance risks that may impact the bottom line. This section must include trends on upcoming legal and compliance changes; changes in the number and severity of risks captured in the risk register; the trend in audit non-conformities; and time to resolve audit improvement tasks, broken down by priority (i.e, High, Medium, Low, etc.). This section addresses several ISO 27001 requirements such as changes in external and internal ISMS issues, changes in needs and expectations of interested parties, trends in nonconformities and corrective actions, trends in audit results, results of risk assessment, and the status of the risk treatment plan.
Each section should be divided in two. On the left, we should include trend-based metrics. More importantly, negatively trending metrics requiring attention should be highlighted using a defined colour-coding scheme. On the right, we should include a SWOT analysis covering the trends and, immediately below, a list of key questions that should be considered in the management review. SWOT analyses are a powerful instrument in the security leader’s toolbox and can be applied in multiple situations, especially when joining a new company.
Finally, questions should be supplemented by decision-making options to be weighted by the management team (including the consequences of each option if taken). Consistently structuring each section will ultimately aid readability and foster familiarity. Below is an example of how such sections can be structured within a PowerPoint presentation:
Execution tips
Aim to run a meeting where everyone has read the report and only decisions need to be debated and taken. It’s counterintuitive, but the aim should not be to present the report. Executives can read after all. If even one member has not read the report, postpone the meeting.
Before the meeting, allow the management team to comment on the report and ask clarifying questions. During the meeting, you should start by summarizing the decisions to be debated. Then you should take management through each question to be discussed. Your role during the meeting is to moderate the debate.
Moreover, you should be ready to provide expert input when the management team requires technical expertise, especially when evaluating the consequences of decisions. You should also be prepared to outline which options the management team should select and why. Use a consistent structure to outline options and consequences, both verbally and in writing, like so:
- Option A - Do nothing: Consequences
- Option B - Easy option: Probability of achieving goal in relation to lower costs and complexity
- Option C - Hard option: Probability of achieving goal in relation to higher cost and complexity
Once the decisions are taken, you should capture them in the meeting minutes and share them with the management team for review and confirmation. It’s that simple.
Conclusion
Lean reviews will involve management and empower them to do what they do best: make decisions about risk. Over time this will build their confidence in you and in security being delivered with agility, rapidity and efficiency. They will open up security activities to quarterly scrutiny, increasing visibility on their broader strategic impact, rather than just the impact on the bottom line. Finally, it will give your team the confidence, tools, and mandate to get stuff done with management’s full blessing.