Scenario-based threat management
Cut out the noise, address what matters and efficiently manage threats using lean, scenario-based approaches

When identifying and prioritising threats, cybersecurity teams have many options available. Plenty of platforms, frameworks, and techniques exist to help prioritise the constant stream of threats that companies face. The problem is that there are too many options available, and many are cost-prohibitive. Consequently, small and medium-sized enterprises (SMEs) can be rapidly overwhelmed by these options, making it difficult to identify easy-to-implement, cost-efficient, yet effective threat management approaches.
In cybersecurity, threat management refers to continuously identifying, analyzing, and mitigating cyber threats to protect an organisation’s digital assets, networks, and systems. It is a critical part of cyber risk management and includes multiple security disciplines.
Traditionally, there are three threat management approaches that stand out. The first is Threat Modelling, a structured approach to identifying potential threats and vulnerabilities in a system. Two well-known methodologies are PASTA (Process for Attack Simulation and Threat Analysis) and STRIDE (Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, Elevation of Privilege). While threat modelling offers an excellent approach to managing threats, it suits technology companies offering digital products and running an established secure software development lifecycle (SSDLC). It requires mature software development and asset management processes, which cost time and money.
The second is Threat Intelligence, which helps defend against attacks by collecting and analysing information about emerging cyber threats. While threat intelligence is frequently mentioned in the marketplace, it is often overkill for SMEs. Successfully implementing a threat intelligence program requires significant investment in talent and resources, making it impractical for smaller organisations.
Finally, there are frameworks such as MITRE ATT&CK, a knowledge base of adversary tactics and techniques based on real-world observations. While ATT&CK is a powerful specialist framework, it is primarily useful for detection engineers rather than a broad audience. It is low-level and highly technical, making it difficult for SMEs to implement quickly and efficiently.
Threat management for lean teams
All approaches discussed above have unique strengths and are used daily in the industry. However, they are hard to implement effectively without specialist expertise. More importantly, they are often useful to specialist audiences rather than providing a broad, organisation-wide tool to describe the impact of attacks.
A lean and efficient threat management approach should be cheap, meaning it should be financially efficient and not require heavy personnel investment. It must also be fast, guaranteeing quick adoption and ensuring rapid results by embedding security in the early stages of software development/project management. Finally, it should be accurate, producing actionable threat management strategies that can be implemented quickly using existing solutions.
Unfortunately, none of the existing approaches are simultaneously cheap, fast, and accurate. For example, a fast and cheap solution like subscribing to a free threat intelligence feed is unlikely to produce accurate results. A fast and accurate solution like a mature threat intelligence program is not cheap to implement. It will require significant upfront investment. A cheap and accurate solution like building an in-house threat intelligence program is not fast. It will have to be built piecemeal over many years.
A leaner, more effective approach is to employ scenario-based threat management. This approach shifts from traditional threat modelling to a more pragmatic method emphasizing visualization, intelligence integration, and decision support. It originates from systems thinking, a holistic approach to problem-solving that views complex systems as interconnected components.
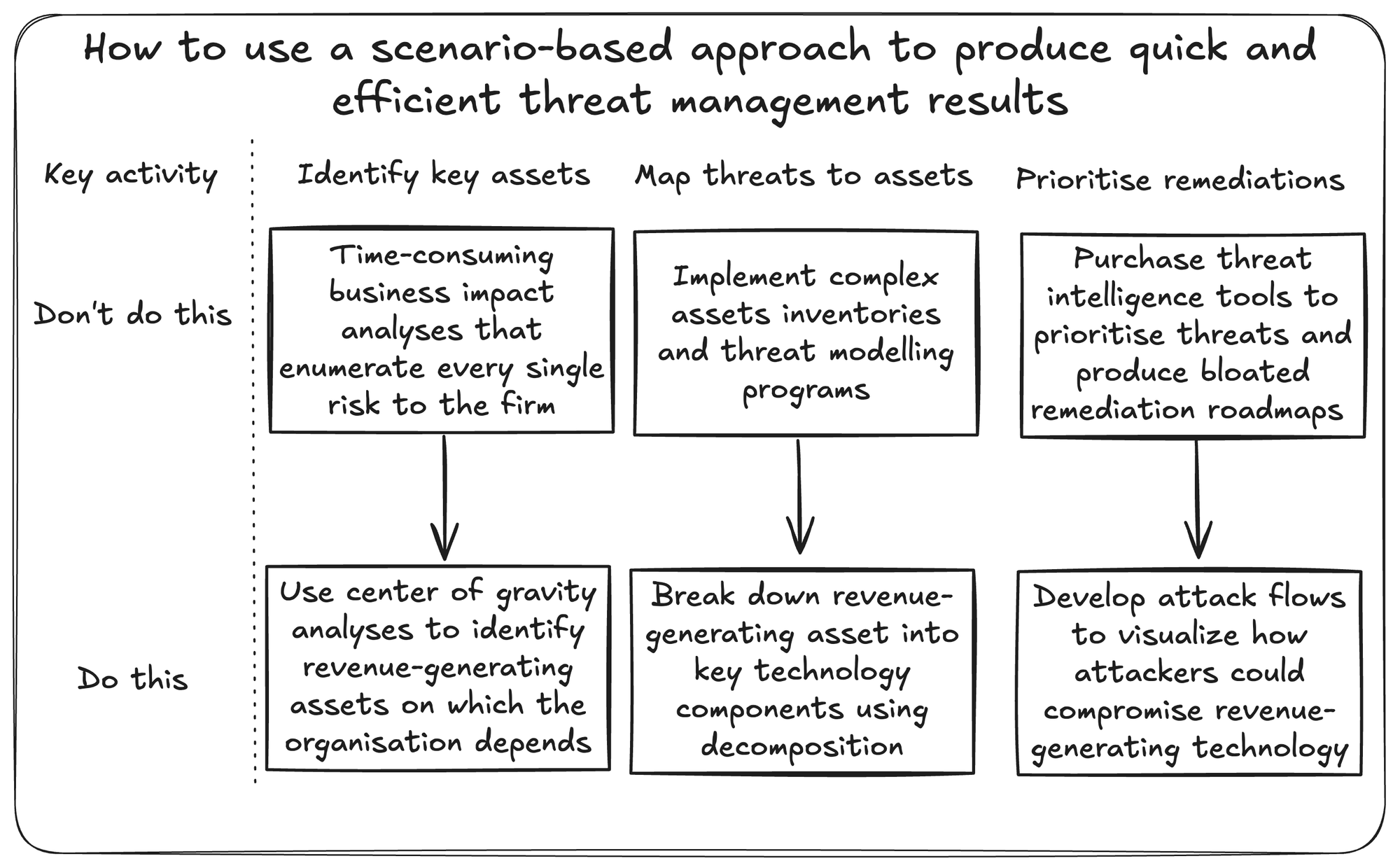
Using a scenario-based approach, smaller security teams can rapidly identify threats and countermeasures in three phases:
- Asset identification: identify the company’s centre of gravity to quickly identify revenue-generating assets on which the organisation depends that must be proactively protected.
- Asset decomposition: break down each revenue-generating asset into key technology components using decomposition.
- Scenario modelling: develop attack flows to visualise how an attacker could compromise technology using tactics and techniques based on real-world observations.
Security teams can rapidly bootstrap scenario modelling by sourcing prebuilt scenarios available online. Once open source scenarios have been considered, more advanced scenario content can be purchased through specialist firms, such as Venation (see an example below).
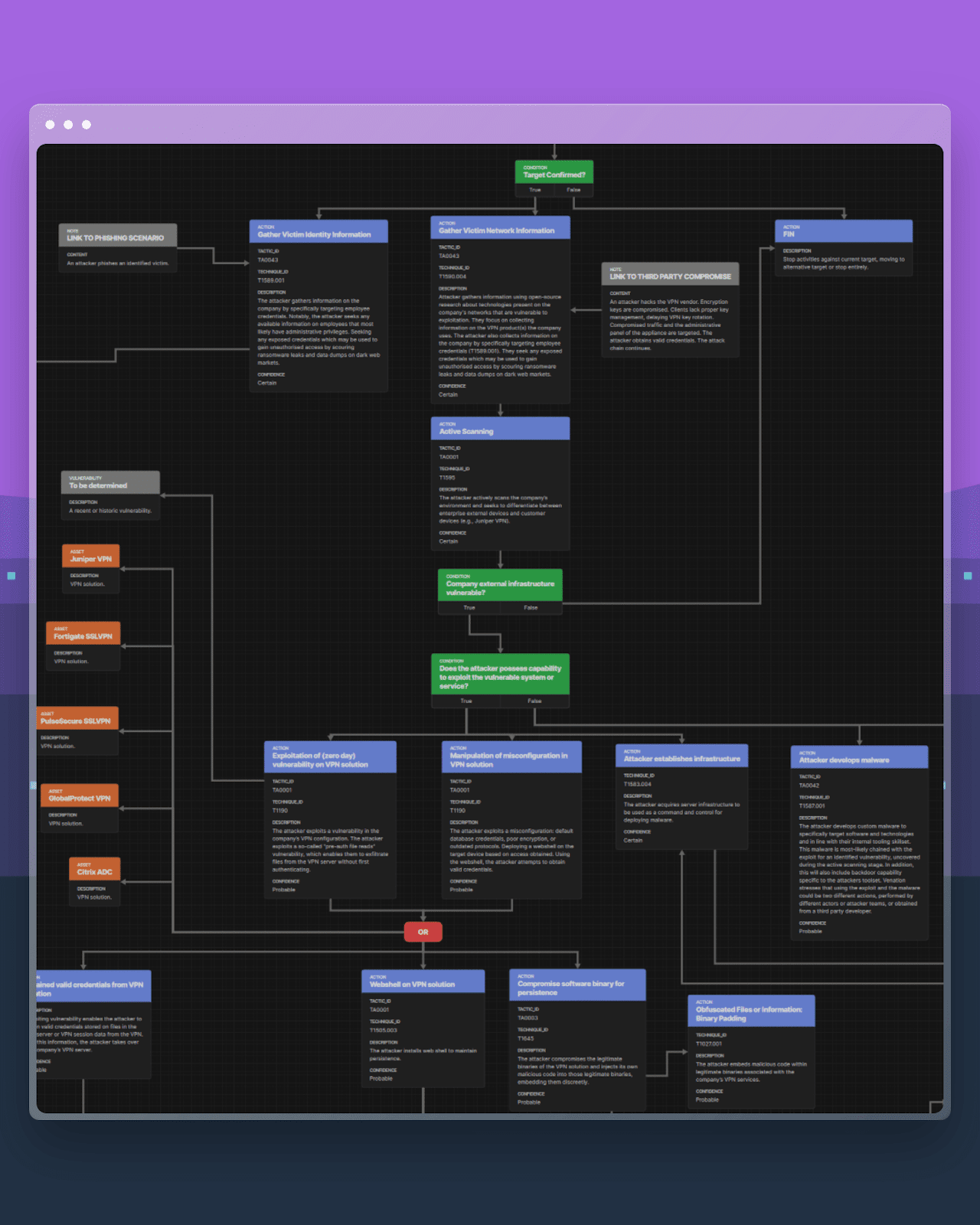
More importantly, this approach immediately links business-critical assets to security measures, while explaining attack sequences in a language that is intuitive across stakeholder groups. At the highest level, scenarios and attack flows can provide executives (CFO, CISO, CIO) with high-level visualisations to communicate risks and strategic decisions. Operations Directors working in Risk Management, Cyber Defence or Incident Response can employ attack flows as an enabler for realistic risk assessments, purple team exercises and mapping of security controls or investments mapping. At the technical level, operators and practitioners (such as Threat Intelligence Analysts, Red Team operators and Incident Responders) can use machine-readable attack flows and the behaviour-based intelligence within to enhance emulation and response efforts.
Using scenario-based threat management, organisations can align stakeholders with a common visual language for security discussions, accelerating effective risk mitigation and threat management discussions across all levels.
An example: SaaS threat management
As an example we can consider a SaaS company with 150-200 employees delivering a single cloud-based product. Let’s assume that such a SaaS company also employs a small security team of 3-4 members that isn’t running a formal security program. Despite this, the team must deliver threat management advice across several stakeholder groups quickly. In such a case, a scenario-based approach could enable the team to rapidly identify and propose security improvements without a costly or complex security strategy.
As a first step, instead of performing a time-consuming and thorough business impact analysis, the team can perform a simple center of gravity analysis.
This analysis will help identify critical assets that support revenue-generating operations and, hence, are essential to the business. For our example company, the SaaS product would be surely identified as one of the core business assets since, in case of compromise, revenue and customer trust would be at risk.
In the second step, the team would analyse the SaaS product and break it down into key technology components, encompassing both the frontend and backend, through a decomposition analysis. The product’s front end would probably consist of a React-based web application. It could also include additional frameworks such as Angular or Vue.js, as well as dependencies on content delivery networks (CDNs) and external APIs.
The backend infrastructure could be built on a Debian-based Kubernetes cluster and further incorporate database management systems like PostgreSQL or MongoDB, caching layers such as Redis, authentication services like OAuth or OpenID Connect, and cloud provider services for storage and compute power.
By decomposing the application and understanding its complete technology stack, the security team would identify potential attack vectors across the entire SaaS ecosystem.
In the final step, the team would research attack flows for each major application component. Focusing on Kubernetes, the team would employ a scenario-based approach to identify known attack paths within the technology. Once attack paths are mapped, critical defence choke points can be identified. If possible, the team can also integrate threat intelligence about Kubernetes-specific threats, ensuring that defensive strategies also target emerging attack trends. Finally, the team could map security controls and configurations with industry standards such as ISO, NIS2, and DORA. This would lay the groundwork for more formal governance, risk management and compliance (GRC) activities planned for the future.
Based on the attack flows, the team would then prioritise efforts to address high-impact risks early in the attack chain, helping reduce the attack surface in an effective and cost-efficient manner.
For example, during a first round remediation effort they might advise the business to harden existing Kubernetes role-based access control policies to mitigate privilege escalation risks. Similarly, they could provide concrete guidance to restrict API access, enforce network segmentation and improve container logging.
By visualising attack scenarios, the security team would communicate such improvements by describing, step-by-step, the different stages of the attack. By avoiding technical language and using intuitive scenarios, they would accelerate rapid buy-in and coordination momentum across several stakeholder groups.
Conclusion
Scenario-based threat management provides a lean, efficient, and highly effective alternative to traditional security approaches. By focusing on business-critical assets, relevant technologies, and realistic attack flows, small companies can implement meaningful security measures quickly and cost-effectively.
Even for large enterprises struggling with threat management, a scenario-based approach offers a practical way to enhance cybersecurity without significant investment in personnel or expensive tools.




