How to start a cybersecurity program
Creating a cybersecurity program does not have to be an expensive and complex challenge. Find out how in this post
Cybersecurity, how to get started? During the fall of 2023, this is one of the most searched questions on the web. For many companies, implementing a cybersecurity program is now becoming a mandatory requirement.
In Europe, pressure for companies to improve their cybersecurity had already increased with the entry into force of GDPR regulations in spring 2016. With the imminent arrival of the Cyber Resilience Act, European companies will need to adjust their infrastructure and production to ensure they develop and sell secure products on the market.
Although the Cyber Resilience Act largely appears to focus on securing production processes, it is clear that in order to produce secure products, the company itself must be secure. A cyber intrusion at company level can, eventually, lead to the compromise of the production chain itself, regardless of the investments made to secure it.
Faced with this new regulatory challenge, companies (especially medium-sized businesses) are having to consider implementing their own cybersecurity programs. Initiating such a program may seem, at first, to be an expensive and complex challenge. In fact, many companies tend to think that it takes a lot of money to get such a program off the ground.
Fortunately, by knowing where to look and what to do, one can avoid, at least in the early stages, to spend large amounts of time and money. By taking a minimalist approach and focusing on the simplest basics of cybersecurity, one can achieve excellent results right away. You can also do this without requiring the creation of a new item in the company budget, but simply by intelligently directing the focus of your IT team, or that of your IT vendors.
Identifying an initial reference framework
A quick google search will help you discover two widely used frameworks for defining cybersecurity programs: CIS Controls and NIST cybersecurity framework.
Both are de facto standards within the cybersecurity world, they define all the necessary technical controls that a company must develop as part of their cybersecurity program.
Of the two, CIS controls is the most lightweight. Created by the Center for Internet Security, it is structured around 18 technical controls to implement to improve corporate IT resilience. The framework starts from basic controls such as management of hardware and software inventories, data protection and secure system configurations all the way to advanced topics such as incident readiness and penetration testing activities.
In contrast, the NIST cybersecurity framework represents the most comprehensive framework. Created by the National Institute of Standards and Technology, it is based primarily on 5 technical areas, each representing a specific capability to be developed within cybersecurity programs, as shown in the image below:
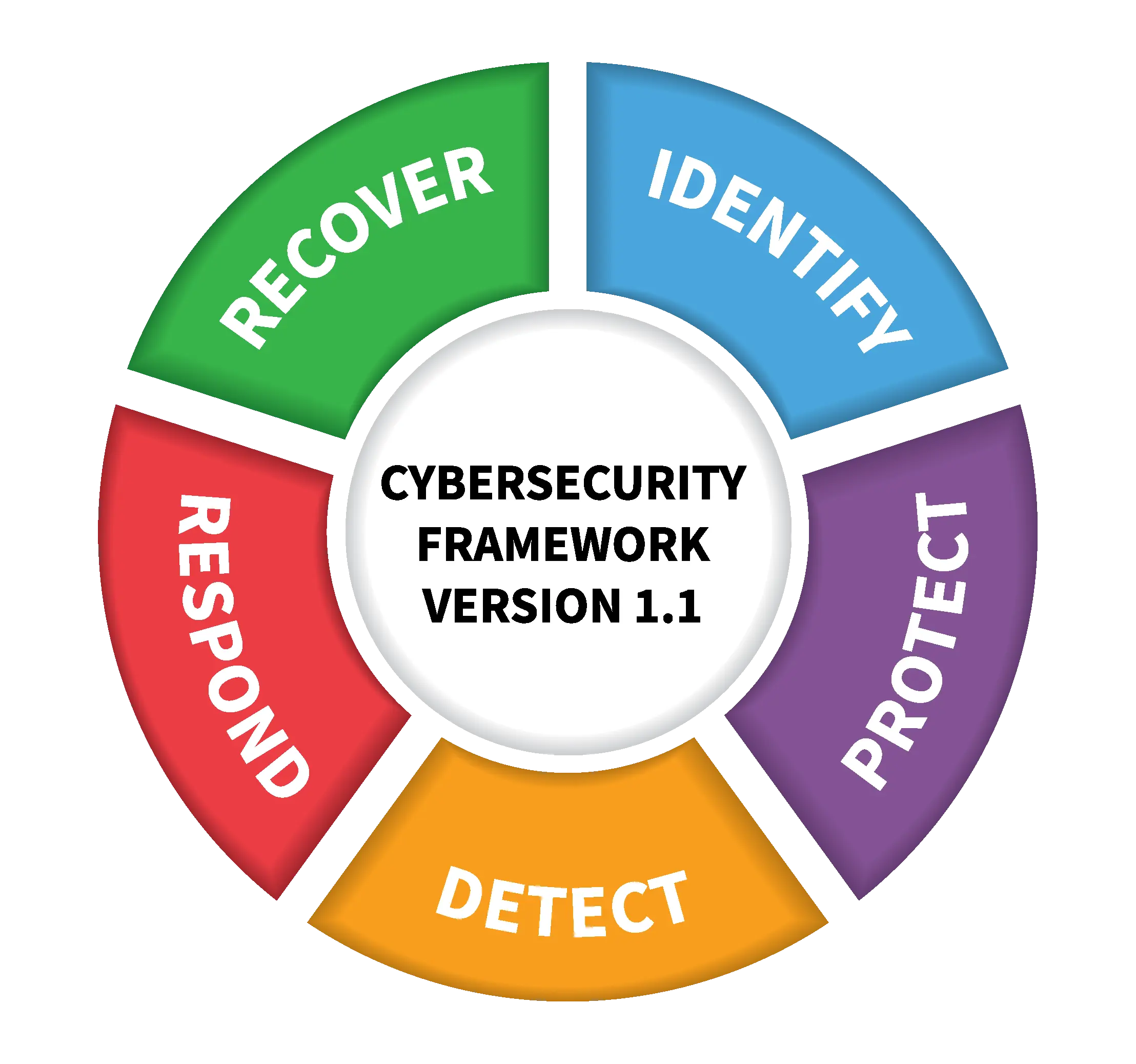
Within each technical area, the NIST framework lists 4 to 6 technical controls to implement in your program. The NIST framework is generally used to structure large-scale cybersecurity programs and is primarily encountered within large corporations.
Despite their usefulness, the two frameworks are really aimed at companies that intend to invest heavily in their cyber defense and resilience. For small and medium-sized enterprises the two frameworks are excessively complex and of little use in defining a strategy to be rapidly implemented at low cost.
This has been noticed by the British government, which, through its National Cybersecurity Centre, has defined a specific framework for small and medium-sized businesses called Cyber Essentials.
This framework directs companies to focus on five essential areas, all of which are useful in developing basic, yet solid, cybersecurity capabilities. The framework specifically recommends the implementation of network protections (firewalls and Internet gateways), secure configuration of hardware and software assets, controlled access to data, installation of antivirus software, and implementation of a vulnerabiliy management program.
The Cyber Essentials framework provides an excellent starting point for defining an initial strategy. However, to completely eliminate costs and rapidly implement a program, an even more compact framework should be defined, Moreover, it should be optimized toward the re-use of existing resources and workstreams within the company.
Defining the program
Starting with Cyber Essentials we can define a compact program that is easily “sellable” within the company or, alternatively, to its IT suppliers. The program should have as a central goal the protection of corporate data and should be structured around four basic points, as shown below:
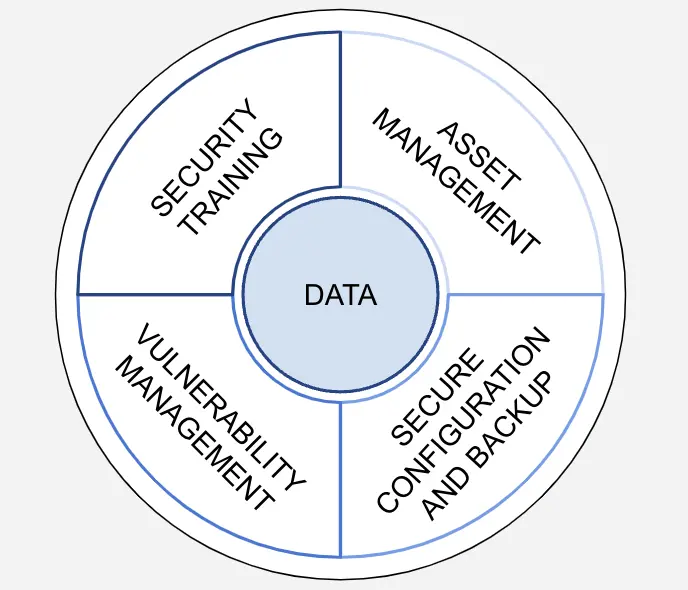
Four key capabilities or areas are defined within the program. Each contributes to improving the company’s data protection and overall IT resilience by focusing on the following aspects:
- Asset management: the ability to recover from cyber attacks depends in large part on a thorough understanding of a company’s IT systems and which ones, in particular, the company depends on to survive. Therefore, a catalog of hardware and software assets becomes central not only to manageme the IT ecosystem, but also to ensure the overall effectiveness of a company’s cybersecurity program (as will be seen later).
- Secure configuration and backup: the program must include a process for creating secure configurations for IT systems. Within this area, we must also include the reviewing and improving of access to company data, both by system administrators and employees. Finally, the establishment of a backup strategy should be included to guarantee data recovery in the event of a cyber attack.
- Vulnerability management: central to a cybersecurity program is the management of vulnerabilities in enterprise software. Without a program to track and aggressively remediate software vulnerabilities, a company will undoubtedly suffer more cyber attacks. To contain or, rather, prevent emergency response costs, a vulnerability management program must be included within our basic program.
- Training: staff training is the last pillar of our core strategy. The lack of staff that is trained and aware of cybersecurity risks, in fact, completely negates the benefits gained from the first three pillars. Without proper training, the company relies on staff that is unable to recognize and respond appropriately to suspicious activity on company networks.
Such a structured program would bring the following benefits:
- Simplicity: because of its simple structure, the program makes use of initiatives that are well known within the IT world and do not require the input (or hiring) of cybersecurity experts.
- Ease and speed of implementation: the simplicity of the program should make it easy to implement within rapid timelines. There is no need to divert IT resources or hire new ones: just redirect your IT team’s focus on implementing these initiatives by setting goals that align with the pillars of the program. If you are relying on outside vendors, you can use the pillars to audit your vendor’s internal practices to ensure your cybersecurity requirements are met.
- Low cost and highly promotable: Considering the points listed above and the absence of additional costs, the program should be easily promotable within the company and easily approved by management.
- Alignment with international standards: using Cyber Essentials, NIST and CIS as a starting point, the implementation of this basic program would put a company in a solid starting position to grown its cybersecurity maturity over time. finally, the program would lay the groundwork for obtaining international cybersecurity certifications such as ISO27001 and ISAE3000.
Asset management
The first step to increase cyber resilience is to assemble a catalog of IT assets in use within the company (commonly called an Information Technology Asset Management (ITAM) inventory). Usually, the absence of a single source of truth tracking company IT assets is a major factor in causing longer incident remediation times.
For example, if a company is successfully compromised through a malicious software program, without an ITAM inventory it becomes much more difficult and costly to trace the path of the attack within the network to find the origin device. In addition, failure to identify the attack source could compromise the ability your company’s understanding of the cause of the attack.
For small and medium-sized businesses, creating an ITAM inventory does not necessarily require the purchase of dedicated software. You can safely start with an Excel document and consider purchasing dedicaed software later. A great initial template can be downloaded here.
For large companies that rely on traditional IT environments (connected via domains and directories) it becomes almost mandatory to purchase dedicated software to provide the necessary automation for effective and scalable inventorising. Solutions typically used in these contexts are known to be offered by ServiceNow and Atlassian.
For companies (large or small) that primarily use cloud solutions for productivity (such as Google Workspace), the situation becomes more challenging.
While such companies can create an inventory of hardware assets through Excel (or by purchasing dedicated software), automatic cataloging of all cloud platforms used by employees becomes much more difficult when cloud platforms are used; especially if Single-Sign-On authentication is used.
The use of Single-Sign-On can generate an uncontrolled proliferation of cloud platforms used in the company, resulting in increased costs and the introduction of platforms that process data in ways that are potentially incompatible with European privacy regulations. In this case, companies can only rely on dedicated solutions to maintain control. An excellent solution for cataloging and managing cloud platforms is offered by Zluri, but there are others available on the market.
If, on the other hand, you rely on a third party to manage your IT systems, the matter becomes simpler: just ask the vendor for an updated copy of their inventory of assets used to provide services to your company so that you can compare it against your own inventory.
Finally, to create an ITAM catalog that adequately supports your cybersecurity program, the following steps should be taken:
- Highlight the company’s crown jewels: in your inventory you should highlight all those assets (servers, platforms or ICS/SCADA systems) that are critical to the survival and operation of the company. A thorough knowledge of these systems will help establish more focused security controls. Additionally, in the event of an incident, knowledge of your crown jewels will allow your IT team to quickly analyze its impact: an attack against a business-critical system will have, in fact, a greater impact compared to, say, an attack against a peripheral system.
- Establish a quarterly review cycle: your inventory will need to be reviewed regularly, especially if you do not employ automated solutions. Generally speaking, a quarterly review should be more than sufficient. In addition, your IT team should document the review process to ensure continuity in case of staff absences or resignations.
- Establish a system of ownership: your catalog should include a system for cataloging IT assets via ID codes. In addition, the IDs should attribute company assets to business departments rather than individuals. This would ensure ownership information remains unaffected by staff absences, resignations or changes.
- Establish a lifecycle tracking system: establishing a system to tracks the lifecycle of an IT asset is even more important. Defining the key stages of an asset’s life within your company is critical to understanding whether the asset is in active use. Such tracking can also prove invaluable in the event of a cyber attack. Your IT team will, in fact, be able to adjust incident response actions depending on the type of affected devices.
Secure configuration and backup
The second area of the program plays a key function in guaranteeing a rapid recovery capability against cyber attacks. It consists of two elements:
- Secure Configuration: the creation of standardized security-focused configurations ensures that your company deploys to production devices that are hardened against cyber attacks. Additionally, standardized configurations ensures a reduction in hardening errors or the accidental introduction of security holes by the IT team.
- Backup strategy: the implementation of a backup strategy, applied consistently and rigorously, offers the best guarantee for rapid recovery in the event of an attack. It should be regarded as an insurance against cyber attacks, but also in the case of operational issues: your IT team will be able to quickly recover any device by simply re-updating the operating system to a working version before the attack/technical issues occurred.
Plenty of recommendations are available online on how to create secure configurations. CIS, for example, provides a public database, free of charge, (called CIS benchmarks) containing lists of standardized secure configurations for desktop software, mobile devices, networking devices, and more.
Because the configurations distributed by CIS are extremely detailed and inclusive, CIS offers compilation kits to automate hardening configurations. Such kits are designed to cover most benchmark settings. However, because benchmark templates and installation software do not contain all possible configurations, they should still be reviewed and, if necessary, modified by your IT team to align with your company’s internal policies.
For cloud environments, the approach changes slightly. In general, the best approach is to rely on vendor documentation. Google, for example, offers excellent security documentation that covers both strategic and architectural considerations. If your company uses Google Worskpace, it should comply with the security checklists that Google makes publicly available. On the other hand, if your company uses Google Cloud products, your IT team should refer to Google’s basic blueprints to ensure your company always deploys secure cloud resources into production.
Many materials are also available online to help with developing a backup strategy. In general, a backup strategy ensures that the company always has a redundancy system for its data and its IT system. By creating back-up copies, such a program ensures that its computer systems can be quickly restored in the event of technical problems, including those caused by a cyber attack.
When creating a backup strategy, the following aspects should be defined:
- Backup time frames that include, at a minimum, the creation of daily, weekly and monthly backups
- A system to regularly review backups (at least on a quarterly basis). moreover, the system should be inspectable and certifiable by external auditors (if necessary to maintain specific ISO certifications)
- A system to certify, through regular testing, the proper functioning of company backups
Of the many resources on the Web that you can use when defining your backup strategy, your company should use CIS control 11 as a starting point. This CIS control, in fact, lists all the basic considerations to be incorporated into your company’s backup strategy.
Vulnerability management
The third area plays a greater role in ensuring a more active, rather than passive, resilience to cyber attacks. A vulnerability management program allows companies to identify and monitor, in real time, all software vulnerabilities and eliminate them quickly through the release of software updates (called patches).
The CIS Controls framework again offers a set of guidelines that can be used free of charge: they are contained within CIS Control number 7 and offer numerous tips for developing a program that minimizes the presence of vulnerabilities within your company’s network.
For cloud environments, it is again advisable to rely on vendor documentation. For example, Microsoft Security provides an excellent selection of guidelines. The Security team at Google, on the other hand, recently released an excellent podcast that “opens the door” on their vulnerability management program.
If you rely on an external IT provider, you should ask them to sen you their guidelines and any contractual provisions (such as, for example, service level agreements, also known as SLAs) describing their vulnerability management process. In fact, this process should be considered an integral part of the services they provide. If your vendor does not provide vulnerability managment services or SLAs, you should insist on the integration of these in your contract to protect the security of your network.
First and foremost, the procedure adopted by your IT team to manage vulnerabilities in the organisation should be described within an overall vulnerability management policy. The policy should contain, at a minimum, the five steps described in the image below:
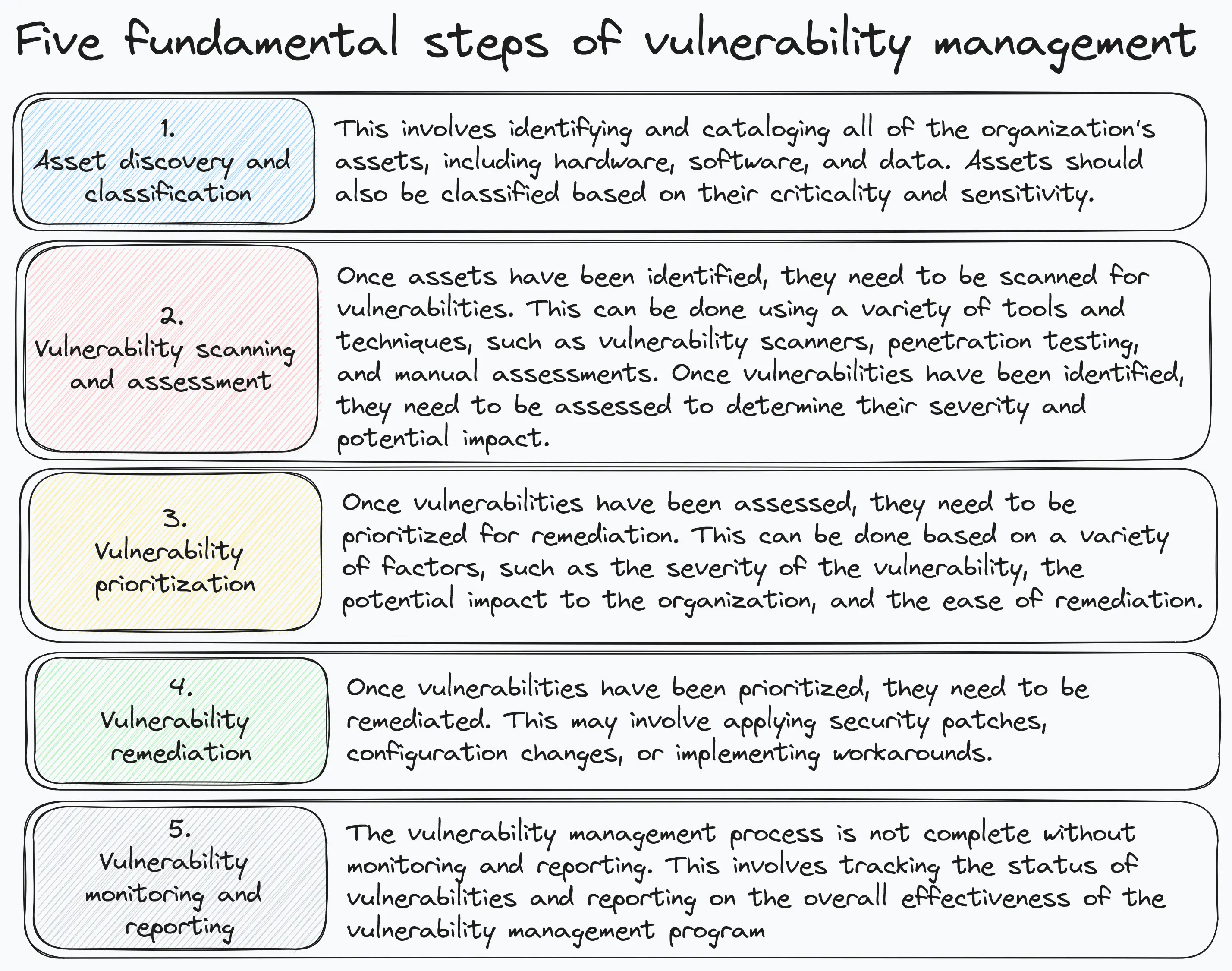
In addition, the program must include:
-
Guidelines for regular scans: vulnerability scans should be run regularly. Scans should be performed automatically and the results reviewed and resolved in a timely manner. There are many commercial vulnerability scanning products available on the market today. At the same time, there are free, open source alternatives such as OpenVAS.
-
Criteria for prioritizing action on vulnerabilities: some vulnerabilities are more serious than others and, therefore, more likely to be exploited. For your vulnerability patching processes to be effective, your team must be able to effectively prioritise resources and response activities. The following factors should be considered when defining prioritization criteria:
- Severity: how severe is the vulnerability? In this case, your IT team can use the CVSS system to assess the severity of vulnerabilities. This system is a de facto standard in the cybersecurity industry, and almost all providers report software vulnerabilities using this system.
- Exploitability: How likely is the vulnerability to be exploited? This criteria should consider factors such as exposure of the software to the public internet, severity of the vulnerability and ease of exploitation.
- Impact: What would be the impact on the company if the vulnerability was successfully exploited? In this case, your ITAM inventory (especially if it identifies corporate crown jewels) becomes critical in determining the impact of a vulnerability on the network depending on the type of asset being compromised.
-
Emergency Response Plan: Once prioritisation criteria have been defined, the program must include a remediation plan. Remediation may involve applying security patches, updating software components, or implementing workarounds.
-
Procedures for installing security patches: the program should describe how security patches from vendors would be deployed by your own IT team. Specifically, the procedure should describe, step by step how security patches are to be applied in the network and within which timeframes.
-
Procedures for program monitoring and review: vulnerability management should be considered an ongoing process. In this regard, the program should define how your IT team continuously monitors systems and applications for new vulnerabilities. In addition, the program must contain a feedback procedure, which allows your IT team to periodically review the vulnerability management program itself in order to identify improvements and to ensure its continued effectiveness.
Security training
The fourth and final area concerns the training of staff through cybersecurity awareness programs.
Security awareness training programs are educational programs designed to make employees aware of cyber threats and to convey techniques for protecting themselves and the organization from such threats. These programs cover a wide range of topics, including phishing, malware, social engineering, password security, and more.
Security awareness training is important because, if well executed, it helps reduce the incidence of cyber attacks involving human vectors, as in the case of phishing and social engineering. Employees are often the first line of defense against these types of attacks, so it is essential that they are trained to recognize the warning signs and respond effectively.
Specifically, the implementation of a security awareness program can bring the following benefits:
- Improved data security: Security training can help improve data security by teaching employees how to protect sensitive data and avoid breaches through attacks or scams that exploit human vectors (as in the case of vishing).
- Reduced compliance costs: Many companies are required to comply with specific privacy and data security regulations. Security training can help such organizations meet these compliance requirements and avoid fines.
- Protects the organization’s reputation: A cyber attack can damage an organization’s reputation and result in the loss of customers and revenue. An effective security awareness program can help protect an organization’s reputation by reducing the risk of cyber attacks and the damage that can result.
Security awareness should be considered an integral part of a cybersecurity program. In this regard, NIST has developed and released NIST Special Publication 800-50 where it specifies the requirements necessary for the development of an effective security awareness program.
Many of the guidelines contained in NIST 800-50 are easy to implement within your own company at no additional cost. If you want to opt for an even simpler solution, you can instruct your IT team to develop a simple, but effective, security awareness program by copying and circulating the security awareness materials made publicly available by the European Union Agency for Cybersecurity (ENISA) during Cybersecurity month. An example of such materials that can be easily packaged in an email can be seen below:

In any case, when creating a cybersecurity awareness program you should follow the below points:
- Adapt the program to the needs of the organization: When creating the program it is worth keeping in mind the types of cyber threats that may affect your organization and the specific responsibilities of your employees. Members of a human resources department must necessarily receive education more focused on the risks related to phishing or vishing, as they will be regularyl handling calls and emails as part of their job duties. On the contrary, a team of programmers can benefit from more advanced training courses. For example, your company’s front-end developers could be trained in recognising and avoiding OWASP TOP 10 vulnerabilities.
- Make the training engaging and interactive: As with any training course, employees are more likely to learn and retain knowledge if training sessions are interactive and engaging. If possible, your program should make use of different training methods, such as online courses, videos, in-person role exercises or, even better, the use of phishing simulations.
- Assess employee knowledge and skills: In addition to creating the program, you must ensure that you regularly test the knowledge and skills acquired by your employees. Typically, these checks can be done via simple questionnaires. In this case, it is advisable to use free services such as SurveyMonkey or Google Forms to complement the training sessions with questionnaires aimed at verifying the knowledge acquired by employees.
- Regularly update training: As cyber threats continue to evolve, you should regularly update your security training program to ensure it covers the latest threats.
In addition to the free resources discussed above, there are also paid providers who specialize in providing security awareness courses. A simple online search can help you quickly identify which providers are available in your region.
As you can see, by following an approach focused on the simplest basics of computer security and using free resources available online, you can create a compact, highly effective and cheap cybersecurity program. Taking the CIS, NIST and Cyber Essentials frameworks as inspiration, you can lay the foundations for pursuing more ambitious cybersecurity programs and aim to obtain international cybersecurity certifications in the future. You simply need to know where to look, what to search for and redirect your existing resources efficiently and wisely.
